
The preparation materials for Microsoft AZ-500 are generally lacking. Can anyone give advice on the exam? The basics are not to say, everyone knows to learn from the Microsoft Learn section. The secret to passing the exam is focused on the details, and the practice test is a huge help, reading all the answers and continuing to accept them until they pass. Pass4itSure AZ-500 exam dumps (Link https://www.pass4itsure.com/az-500.html) provide the most realistic AZ-500 practice test! All issues are verified and trustworthy.
For more Microsoft exam practice tests, stay tuned microsoft-technet.com blog!
Free Best Quality AZ-500 Exam Dumps PDF:
AZ-500 exam pdf free https://drive.google.com/file/d/16_DoJyg-HDQ_nNS1J3qiQiS0mSpJNMou/view?usp=sharing
Shared by Pass4itSure, part of the AZ-500 exam practice questions in the AZ-500 exam dumps PDF. Welcome to download and read, it will be helpful to your exam.
Latest Update Microsoft AZ-500 Exam Online Practice Test [Q1-Q15]
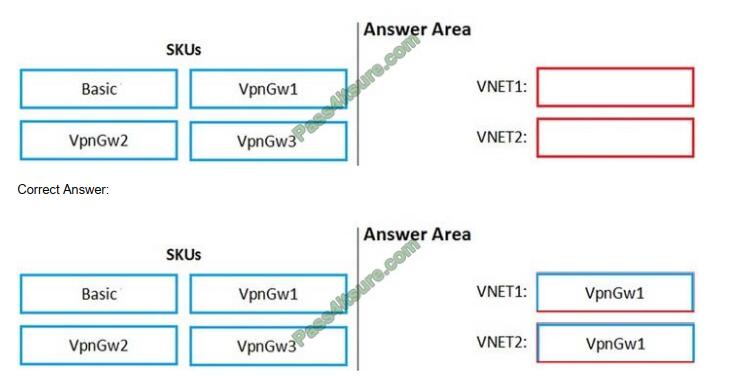
QUESTION 1
You are configuring network connectivity for two Azure virtual networks named VNET1 and VNET2.
You need to implement VPN gateways for the virtual networks to meet the following requirements:
1. VNET1 must have six site-to-site connections that use BGP.
2. VNET2 must have 12 site-to-site connections that use BGP.
3. Costs must be minimized.
Which VPN gateway SKU should you use for each virtual network? To answer, drag the appropriate SKUs to the correct
networks. Each SKU may be used once, more than once, or not at all. You may need to drag the split bar between
panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:
QUESTION 2
You plan to use Azure Monitor Logs to collect logs from 200 servers that run Windows Server 2016.
You need to automate the deployment of the Log Analytics Agent to all the servers by using an Azure Resource
Manager template.
How should you complete the template? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

References: https://blogs.technet.microsoft.com/manageabilityguys/2015/11/19/enabling-the-microsoft-monitoring-agentin-windows-json-templates/
QUESTION 3
SIMULATION
You need to create a web app named Intranet11597200 and enable users to authenticate to the web app by using
Azure Active Directory (Azure AD).
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
1. In the Azure portal, type App services in the search box and select App services from the search results.
2. Click the Create app service button to create a new app service.
3. In the Resource Group section, click the Create a new link to create a new resource group.
4. Give the resource group a name such as Intranet11597200RG and click OK.
5. In the Instance Details section, enter Intranet11597200 in the Name field.
6. In the Runtime stack field, select any runtime stack such as .NET Core 3.1.
7. Click the Review + create button.
8. Click the Create button to create the web app.
9. Click the Go to resource button to open the properties of the new web app.
10. In the Settings section, click on Authentication / Authorization.
11. Click the App Service Authentication slider to set it to On.
12. In the Action to take when the request is not authentication box, select Log in with Azure Active Directory.
13. Click Save to save the changes.
QUESTION 4
HOTSPOT
You have an Azure subscription that contains an Azure key vault named ContosoKey1.
You create users and assign them roles as shown in the following table.
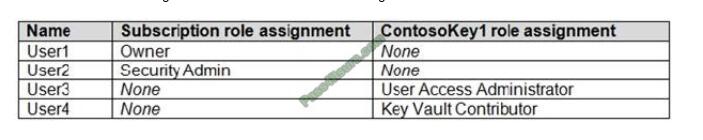
You need to identify which users can perform the following actions:
1. Delegate permissions for ContsosKey1.
2. Configure network access to ContosoKey1.
Which users should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
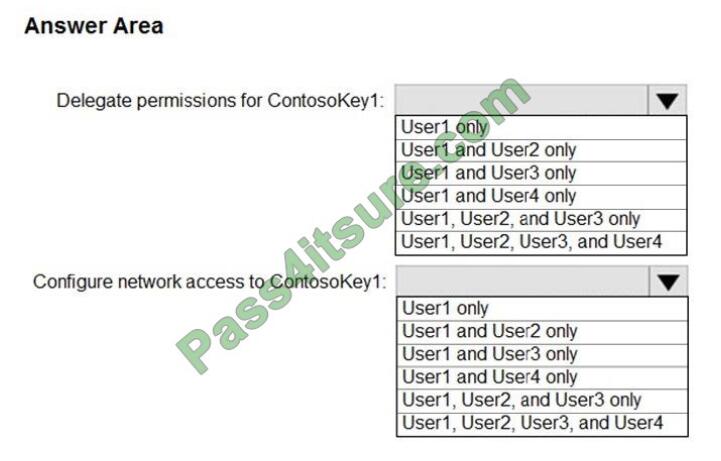
Correct Answer:
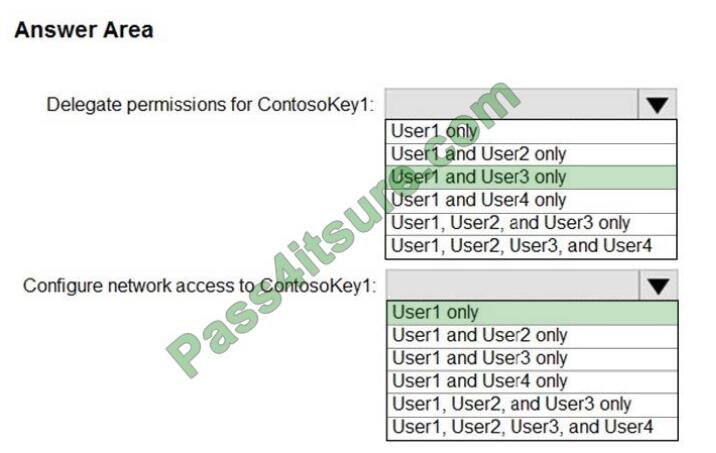
Reference: https://docs.microsoft.com/en-gb/azure/key-vault/general/rbac-guide
QUESTION 5
You have Azure Resource Manager templates that you use to deploy Azure virtual machines.
You need to disable unused Windows features automatically as instances of the virtual machines are provisioned.
What should you use?
A. device configuration policies in Microsoft Intune
B. an Azure Desired State Configuration (DSC) virtual machine extension
C. application security groups
D. Azure Logic Apps
E. security policies in Azure Security Center
F. device compliance policies in Microsoft Intune
Correct Answer: B
You can use Azure Automation State Configuration to manage Azure VMs (both Classic and Resource Manager), on-premises VMs, Linux machines, AWS VMs, and on-premises physical machines.
Note: Azure Automation State Configuration provides a DSC pull server similar to the Windows Feature DSC-Service so
that target nodes automatically receive configurations, conform to the desired state, and report back on their
compliance.
The built-in pull server in Azure Automation eliminates the need to set up and maintain your own pull
server. Azure Automation can target virtual or physical Windows or Linux machines, in the cloud or on-premises.
Reference: https://docs.microsoft.com/en-us/azure/automation/automation-dsc-getting-started
QUESTION 6
SIMULATION
You need to collect all the audit failure data from the security log of a virtual machine named VM1 to an Azure Storage
account. To complete this task, sign in to the Azure portal. This task might take several minutes to complete You can perform other tasks while the task completes.
A. See the below.
Correct Answer: A
Step 1: Create a workspace
Azure Monitor can collect data directly from your Azure virtual machines into a Log Analytics workspace for detailed
analysis and correlation.
1. In the Azure portal, select All services. In the list of resources, type Log Analytics. As you begin typing, the list filters
based on your input. Select Log Analytics workspaces.
2. Select Create, and then select choices for the following items:
3. After providing the required information on the Log Analytics workspace pane, select OK.
While the information is verified and the workspace is created, you can track its progress under Notifications from the
menu.
Step 2: Enable the Log Analytics VM Extension
Installing the Log Analytics VM extension for Windows and Linux allows Azure Monitor to collect data from your Azure
VMs.
1. In the Azure portal, select All services found in the upper left-hand corner. In the list of resources, type Log Analytics.
As you begin typing, the list filters based on your input. Select Log Analytics workspaces.
2. In your list of Log Analytics workspaces, select DefaultWorkspace (the name you created in step 1).
3. On the left-hand menu, under Workspace Data Sources, select Virtual machines.
4. In the list of Virtual machines, select a virtual machine you want to install the agent on. Notice that the Log Analytics
connection status for the VM indicates that it is not connected.
5. In the details for your virtual machine, select Connect. The agent is automatically installed and configured for your Log Analytics workspace. This process takes a few minutes, during which time the Status shows Connecting.
After you install and connect the agent, the Log Analytics connection status will be updated with This workspace.
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm
QUESTION 7
You have an Azure web app named webapp1.
You need to configure continuous deployment for webapp1 by using an Azure Repo.
What should you create first?
A. an Azure Application Insights service
B. an Azure DevOps organizations
C. an Azure Storage account
D. an Azure DevTest Labs lab
Correct Answer: B
To use Azure Repos, make sure your Azure DevOps organization is linked to your Azure subscription.
Reference: https://docs.microsoft.com/en-us/azure/app-service/deploy-continuous-deployment
QUESTION 8
You have an Azure subscription named Sub1 that is associated with an Azure Active Directory (Azure AD) tenant named
contoso.com. An administrator named Admin1 has access to the following identities:
1. An OpenID-enabled user account
2. A Hotmail account
3. An account in contoso.com
4. An account in an Azure AD tenant named fabrikam.com
You plan to use Azure Account Center to transfer the ownership of Sub1 to Admin1.
To which accounts can you transfer the ownership of Sub1?
A. contoso.com only
B. contoso.com, fabrikam.com, and Hotmail only
C. contoso.com and fabrikam.com only
D. contoso.com, fabrikam.com, Hotmail, and OpenID-enabled user account
Correct Answer: C
When you transfer billing ownership of your subscription to an account in another Azure AD tenant, you can move the
subscription to the new account\'s tenant.
If you do so, all users, groups, or service principals who had role-based access (RBAC) to manage subscriptions and their resources lose their access. Only the user in the new account who accepts your transfer request will have access to manage the resources.
Reference: https://docs.microsoft.com/en-us/azure/billing/billing-subscription-transfer
https://docs.microsoft.com/en-us/azure/billing/billing-subscription-transfer#transferring-subscription-to-an-account-inanother-azure-ad-tenant
QUESTION 9
HOTSPOT
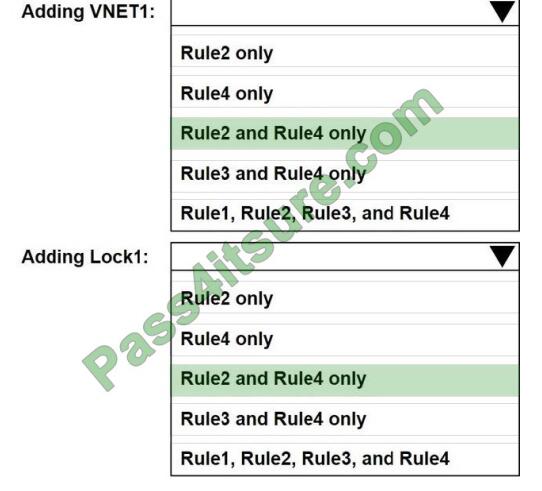
You have an Azure subscription that contains a user named Admin1 and a resource group named RG1.
In Azure Monitor, you create the alert rules shown in the following table.
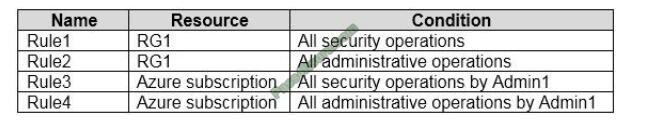
Admin1 performs the following actions on RG1:
1. Adds a virtual network named VNET1
2. Adds a Delete lock named Lock1
Which rules will trigger an alert as a result of the actions of Admin1? To answer, select the appropriate options in the
answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
QUESTION 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not
appear in the review screen.
You have an Azure Subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or
Windows Server 2016.
You need to deploy Microsoft Antimalware to virtual machines.
Solution: You add an extension to each virtual machine.
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
You can use Visual Studio to enable and configure the Microsoft Antimalware service. This entails selecting Microsoft
Antimalware extension from the dropdown list under Installed Extensions and click Add to configure with default
antimalware configuration.
References: https://docs.microsoft.com/en-us/azure/security/fundamentals/antimalware
QUESTION 11
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain.
You have an Azure subscription named Sub1 that is associated with an Azure Active Directory (Azure AD) tenant named
contoso.com.
You plan to deploy Azure AD Connect and to integrate Active Directory and the Azure AD tenant.
You need to recommend an integration solution that meets the following requirements:
1. Ensures that password policies and user login restrictions apply to user accounts that are synced to the tenant
2. Minimizes the number of servers required for the solution. Which authentication method should you include in the
recommendation?
A. federated identity with Active Directory Federation Services (AD FS)
B. password hash synchronization with seamless single sign-on (SSO)
C. pass-through authentication with seamless single sign-on (SSO)
Correct Answer: B
Password hash synchronization requires the least effort regarding deployment, maintenance, and infrastructure. This
level of effort typically applies to organizations that only need their users to sign in to Office 365, SaaS apps, and other
Azure AD-based resources. When turned on, password hash synchronization is part of the Azure AD Connect sync
process and runs every two minutes.
Incorrect Answers:
A: A federated authentication system relies on an external trusted system to authenticate users.
Some companies want to reuse their existing federated system investment with their Azure AD hybrid identity solution.
The maintenance and management of the federated system fall outside the control of Azure AD. It\'s up to the
organization by using the federated system to make sure it\'s deployed securely and can handle the authentication load.
C: For pass-through authentication, you need one or more (we recommend three) lightweight agents installed on
existing servers. These agents must have access to your on-premises Active Directory Domain Services, including your
on-premises AD domain controllers.
They need outbound access to the Internet and access to your domain controllers.
For this reason, it\'s not supported to deploy the agents in a perimeter network.
Pass-through Authentication requires unconstrained network access to domain controllers. All network traffic is
encrypted and limited to authentication requests.
References: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta
QUESTION 12
HOTSPOT
You have a file named File1.yaml that contains the following contents.
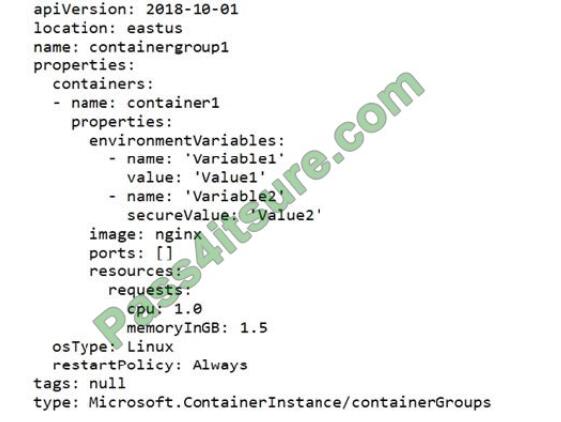
You create an Azure container instance named container1 by using File1.yaml.
You need to identify where you can access the values of Variable1 and Variable2.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Reference: https://docs.microsoft.com/en-us/azure/container-instances/container-instances-environment-variables
QUESTION 13
You have an Azure subscription.
You enable Azure Active Directory (Azure AD) Privileged identify (PIM). Your company\\'s security policy for
administrator accounts have the following conditions:
1. The accounts must use multi-factor authentication (MFA).
2. The account must use 20-character complex passwords.
3. The passwords must be changed every 180 days.
4. The account must be managed by using PIM.
You receive alerts about administrators who have not changed their passwords during the last 90 days. You need to
minimize the number of generated alerts. Which PIM alert should you modify?
A. Roles don\\'t require multi-factor authentication for activation.
B. Administrator aren\\'t using their privileged roles
C. Roles are being assigned outside of Privileged identity management
D. Potential stale accounts in a privileged role.
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-how-toconfigure-security-alerts?tabs=new
QUESTION 14
You have a network security group (NSG) bound to an Azure subnet.
You run Get-AzureRmNetworkSecurityRuleConfig and receive the output shown in the following exhibit.
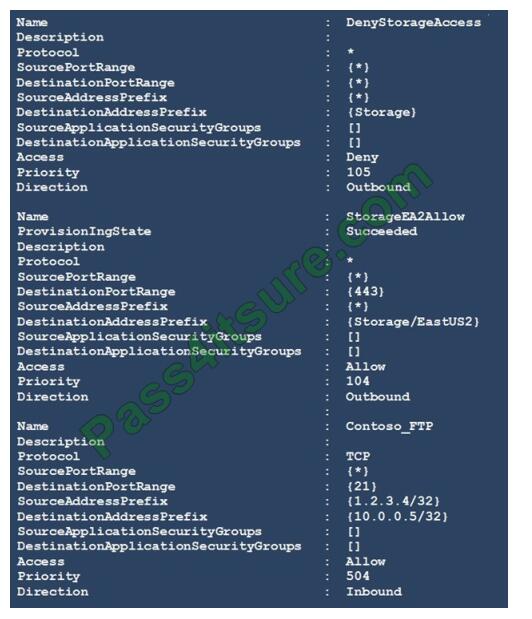
Use the drop-down menus to select the answer choice that completes each statement based on the information
presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:

Box 1: able to connect to East US 2
The StorageEA2Allow has DestinationAddressPrefix {Storage/EastUS2}
Box 2: allowed
TCP Port 21 controls the FTP session. Contoso_FTP has SourceAddressPrefix {1.2.3.4/32} and
DestinationAddressPrefix {10.0.0.5/32}
Note:
The Get-AzureRmNetworkSecurityRuleConfig cmdlet gets a network security rule configuration for an Azure network
security group. Security rules in network security groups enable you to filter the type of network traffic that can flow in
and out of virtual network subnets and network interfaces.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/manage-network-security-group
QUESTION 15
You have an Azure subscription named Sub1 that contains the Azure key vaults shown in the following table:
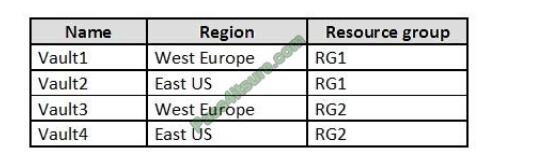
In Sub1, you create a virtual machine that has the following configurations:
1. Name: VM1
2. Size: DS2v2
3. Resource group: RG1
4. Region: West Europe
5. Operating system: Windows Server 2016
You plan to enable Azure Disk Encryption on VM1.
In which key vaults can you store the encryption key for VM1?
A. Vault1 or Vault3 only
B. Vault1, Vault2, Vault3, or Vault4
C. Vault1 only
D. Vault1 or Vault2 only
Correct Answer: A
In order to make sure the encryption secrets don\'t cross regional boundaries, Azure Disk Encryption needs the Key
Vault and the VMs to be co-located in the same region. Create and use a Key Vault that is in the same region as the VM
to be encrypted.
Reference: https://docs.microsoft.com/en-us/azure/security/azure-security-disk-encryption-prerequisites
Want to see more AZ-500 exam questions at Pass4itSure.
PS.
Pass4itSure AZ-500 exam dumps are the learning AZ-500 exam resource you've been looking for. Be careful in the exam, pay attention to the details, the AZ-500 exam success is near. Complete AZ-500 exam dumps question answers in this https://www.pass4itsure.com/az-500.html (Q-As: 320).
These suggestions, I hope they can be useful to you, come on!
Microsoft AZ-104 is one of the most difficult and challenging exams in Azure technology. recommend https://www.pass4itsure.com/az-104.html Other than the proficient preparation, the Microsoft AZ-104 dumps questions are additionally successful. Find useful learning resources for the Microsoft AZ-104 certification exam here: AZ-104 dumps (New In 2020!)
- Microsoft AZ-104 Exam Video
- Microsoft Role-based AZ-104 Exam Questions Answers
- Microsoft AZ-104 Dumps Pdf
Microsoft AZ-104 Exam Video
Microsoft Role-based AZ-104 Exam Questions Answers
With a total of 13 practice questions.
If you are looking for the authentic Microsoft AZ-104 exam questions please see:
QUESTION 1
You have an app named App1 that runs on an Azure web app named webapp1. The developers at your company
upload an update of App1 to a Git repository named GUI. Webapp1 has the deployment slots shown in the following table. 
You need to ensure that the App1 update is tested before the update is made available to users. Which two actions
should you perform? Each correct answer presents part of the solution. NOTE Each correct selection is worth one
point.
A. Stop webapp1 prod.
B. Stop webapp1-test
C. Deploy the App1 update to webapp1-test and then test the update.
D. Deploy the App1 update to webapp1-prod and then test the update.
E. Swap the slots.
Correct Answer: CE
You can validate web app changes in a staging deployment slot before swapping it with the production slot. Deploying
an app to a slot first and swapping it into production makes sure that all instances of the slot are warmed up before
being swapped into production. This eliminates downtime when you deploy your app. The traffic redirection is seamless,
and no requests are dropped because of swap operations. You can automate this entire workflow by configuring auto
swap when pre-swap validation isn\\'t needed. After the swap, you can deploy the App1 update to webapp1-test, and
then test the update. If the changes swapped into the production slot aren\\'t as per your expectation then you can
perform the same swap immediately to get your "last known good site" back. Reference: https://docs.microsoft.com/enus/azure/app-service/deploy-staging-slots
QUESTION 2
You have an Active Directory domain named contoso.com that contains the objects shown in the following table.
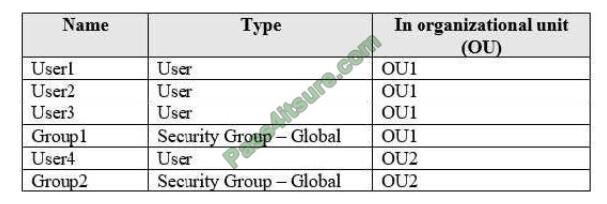
The groups have the memberships shown in the following table.
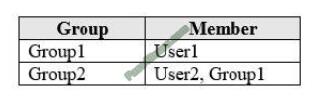
OU1 and OU2 are synced to Azure Active Directory (Azure AD). You modify the synchronization settings and remove
OU1 from synchronization. You sync Active Directory and Azure AD. Which objects are in Azure AD?
A. User4 and Group2 only
B. User2, Group1, User4, and Group2 only
C. User1, User2, Group1, User4, and Group2 only
D. User1, User2, User3, User4, Group1, and Group2
Correct Answer: C
QUESTION 3
You have an Azure subscription that contains the resources in the following table.
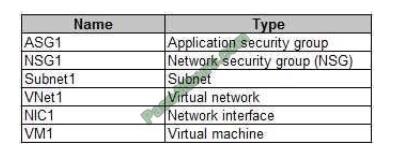
Subnet1 is associated to VNet1. NIC1 attaches VM1 to Subnet1.
You need to apply ASG1 to VM1.
What should you do?
A. Modify the properties of NSG1.
B. Modify the properties of ASG1.
C. Associate NIC1 to ASG1.
Correct Answer: C
Application Security Group can be associated with NICs.
References:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview#application-security-groups
QUESTION 4
You have an Azure subscription that contains the resources shown in the following table.
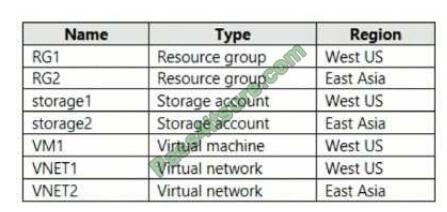
VM1 connects to VNET1.
You need to connect VM1 to VNET2.
Solution: You delete VM1. You recreate VM1, and then you create a new network interface for VM1 and connect it to
VNET2.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
QUESTION 5
You have an Azure subscription named Subscription1 that is used be several departments at your company.
Subscription1 contains the resources in the following table:
Another administrator deploys a virtual machine named VM1 and an Azure Storage account named Storage2 by using a
single Azure Resource Manager template. You need to view the template used for the deployment. From which blade
can you view the template that was used for the deployment?
A. RG1
B. VM1
C. Storage1
D. Container1
Correct Answer: A
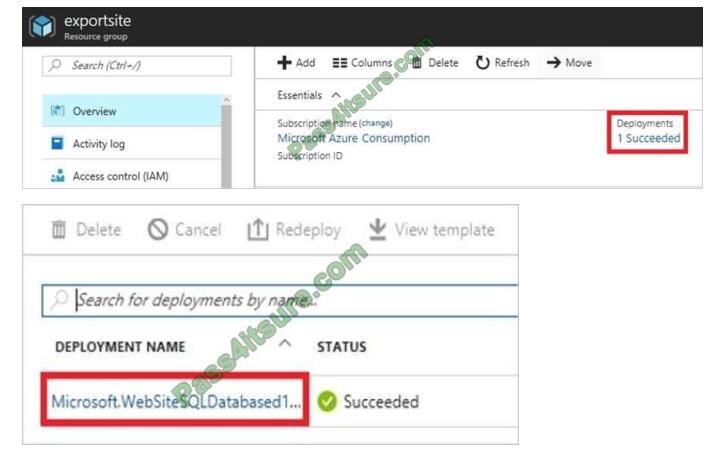
1.
View template from deployment history
Go to the resource group for your new resource group. Notice that the portal shows the result of the last deployment.
Select this link.
2.
You see a history of deployments for the group. In your case, the portal probably lists only one deployment. Select this
deployment.
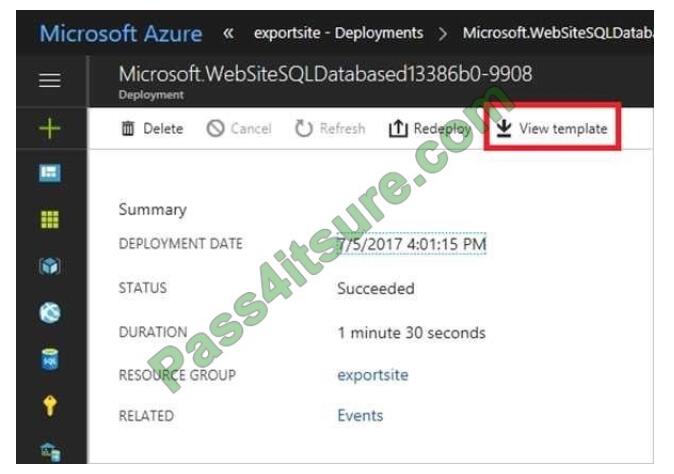
The portal displays a summary of the deployment. The summary includes the status of the deployment and its
operations and the values that you provided for parameters. To see the template that you used for the deployment,
select View template.
References: https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-manager-export-template
QUESTION 6
HOTSPOT
You have an Azure subscription named Subscription1 that contains the resources in the following table.
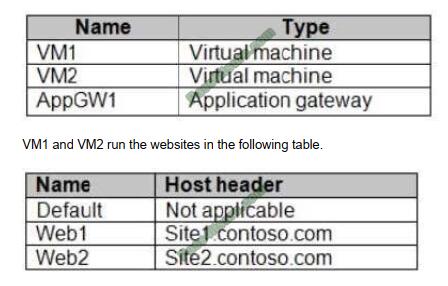
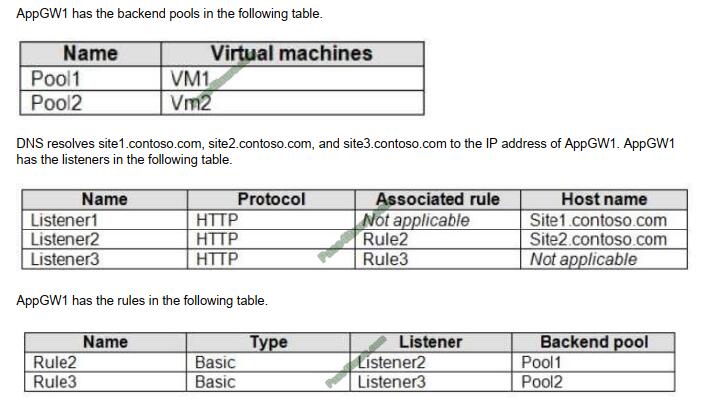
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct
selection is worth one point.
Hot Area:

Correct Answer:

Vm1 is in Pool1. Rule2 applies to Pool1, Listener 2, and site2.contoso.com
QUESTION 7
Your on-premises network contains an Active Directory domain named adatum.com that is synced to Azure Active
Directory (Azure AD). Password writeback is disabled. In adatum.com, you create the users shown in the following
table.
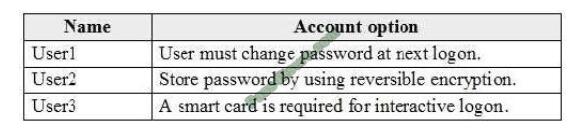
Which users must sign in from a computer joined to adatum.com?
A. User2 only
B. User1 and User3 only
C. User1, User2, and User3
D. User2 and User3 only
E. User1 only
Correct Answer: E
Password writeback is a feature enabled with Azure AD Connect that allows password changes in the cloud to be
written back to an existing on-premises directory in real-time.
References:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-sspr-writeback
QUESTION 8
You have an Azure subscription that contains an Azure Active Directory (Azure AD) tenant named contoso.com and an
Azure Kubernetes Service (AKS) cluster named AKS1. An administrator reports that she is unable to grant access to
AKS1 to the users in contoso.com. You need to ensure that access to AKS1 can be granted to the contoso.com users.
What should you do first?
A. From contoso.com, modify the Organization relationships settings.
B. From contoso.com, create an OAuth 2.0 authorization endpoint.
C. Recreate AKS1.
D. From AKS1, create a namespace.
Correct Answer: B
With Azure AD-integrated AKS clusters, you can grant users or groups access to Kubernetes resources within a
namespace or across the cluster. To obtain a kubectl configuration context, a user can run the az aks get-credentials
command.
When a user then interacts with the AKS cluster with kubectl, they\\'re prompted to sign in with their Azure AD
credentials. This approach provides a single source for user account management and password credentials. The user
can only
access the resources as defined by the cluster administrator.
Azure AD authentication is provided to AKS clusters with OpenID Connect. OpenID Connect is an identity layer built on
top of the OAuth 2.0 protocol. For more information on OpenID Connect, see the Open ID connect documentation.
From
inside of the Kubernetes cluster, Webhook Token Authentication is used to verify authentication tokens. Webhook token
authentication is configured and managed as part of the AKS cluster.
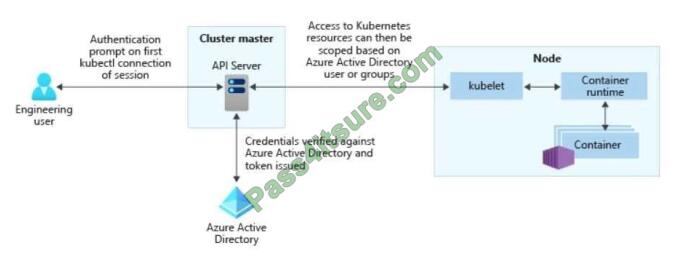
Reference: https://kubernetes.io/docs/reference/access-authn-authz/authentication/ https://docs.microsoft.com/enus/azure/aks/concepts-identity
QUESTION 9
You plan to create the Azure web apps shown in the following table.
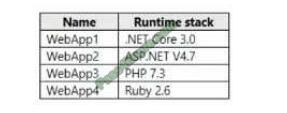
What is the minimum number of App Service plans you should create for the web apps?
A. 1
B. 2
C. 3
D. 4
Correct Answer: D
QUESTION 10
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains
a unique solution that might meet the stated goals. Some question sets might have more than one correct solution,
while others might not have a correct solution. After you answer a question in this section, you will NOT be able to return
to it. As a result, these questions will not appear in the review screen. You manage a virtual network named VNet1 that
is hosted in the West US Azure region. VNet1 hosts two virtual machines named VM1 and VM2 that run Windows
Server. You need to inspect all the network traffic from VM1 to VM2 for a period of three hours. Solution: From Azure
Network Watcher, you create a connection monitor. Does this meet the goal?
A. Yes B. No
Correct Answer: B
Network Watcher Connection Monitor enables you to configure and track connection reachability, latency, and network
topology changes. It helps reduce the amount of time to detect connectivity problems. The returned results can provide
insights into whether a connectivity problem is due to a platform or a user configuration problem. This is not used in
cases where we need to inspect all the network traffic from one VM to another VM. On the other hand Network
Watcher
packet capture allows you to create capture sessions to track traffic to and from a virtual machine. So in this scenario,
we need to use Network Watcher packet capture
References: https://azure.microsoft.com/en-in/updates/general-availability-azure-network-watcher-connection-monitor-in-all-publicregions/#:~:text=Network%20Watcher%20Connection%20Monitor%20helps,or%20a%20user%20con figuration%
20problem
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-packet-capture-manage-portal
QUESTION 11
You need to meet the technical requirement for VM4. What should you create and configure?
A. an Azure Notification Hub
B. an Azure Event Hub
C. an Azure Logic App
D. an Azure services Bus
Correct Answer: B
Scenario: Create a workflow to send an email message when the settings of VM4 are modified. You can start an
automated logic app workflow when specific events happen in Azure resources or third-party resources. These
resources can publish those events to an Azure event grid. In turn, the event grid pushes those events to subscribers
that have queues, webhooks, or event hubs as endpoints. As a subscriber, your logic app can wait for those events from
the event grid before running automated workflows to perform tasks – without you writing any code. References:
https://docs.microsoft.com/en-us/azure/event-grid/monitor-virtual-machine-changes-event-grid-logic-app
QUESTION 12
You deploy an Azure Kubernetes Service (AKS) cluster named Cluster1 that uses the IP addresses shown in the
following table.
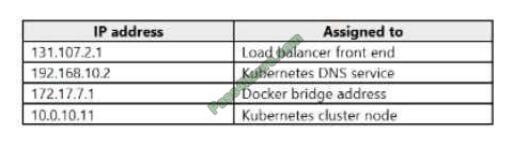
You need to provide internet users with access to the applications that run in Cluster1. Which IP address should you
include in the DNS record for Ousted?
A. 172.17.7.1
B. 131.107.2.1
C. 192.168.10.2
D. 10.0.10.11
Correct Answer: B
When any internet user will try to access the cluster which is behind a load balancer, traffic will first hit to load balancer
front end IP. So in the DNS configuration, you have to provide the IP address of the load balancer.
Reference:
https://stackoverflow.com/questions/43660490/giving-a-dns-name-to-azure-load-balancer
QUESTION 13
You have an Azure subscription named Subscription1 that contains an Azure Log Analytics workspace named
Workspace1.
You need to view the error events from a table named Event.
Which query should you run in Workspace1?
A. Event | where EventType is "error"
B. Event | search "error"
C. select * from Event where EventType == "error"
D. Get-Event Event | where {$_.EventType -eq "error"}
Correct Answer: B
To search a term in a specific table, add in (table-name) just after the search operator Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/log-query/get-started-queries
Microsoft AZ-104 Dumps Pdf
Microsoft AZ-104 Dumps Pdf [Drive] Free https://drive.google.com/file/d/13b_gN3d4XLIS_YmPs3YZHywkUV1JDmm7/view?usp=sharing
You may want to see Microsoft other exams!
Microsoft AZ-104 exam objectives
https://docs.microsoft.com/en-us/learn/certifications/exams/az-104
The objective of this exam measures your ability to accomplish the following technical tasks: manage Azure identities and governance; implement and manage storage; deploy and manage Azure compute resources; configure and manage virtual networking, and monitor and back up Azure resources.
Reason for selection – Pass4itsure

Pass4itsure Discount Code 2020
Get an amazing discount on today.

In the blog post. I will guide you in preparing and pass your AZ-104 exam on the first attempt with ease. I will also link AZ-104 exam dumps https://www.pass4itsure.com/az-104.html (Mock practice tests) which are very helpful for real exams.
Today I passed the exam in 1st attempt.
I have a Data-warehouse and BI experience of over 3 years, which obviously helped.
Questions where you actually have to implement things you learn would be easy you have database experience.
For other questions, the Preparation is good enough. I had one pass over the entire book, but it was a detailed one.
I would say 2 weeks of time is good enough ( if you actually sit and study on all these days Big Smile )
All the best for anyone preparing for this Microsoft https://www.pass4itsure.com/70-461.htmlpdf !!
Exam Code: 70-461
Exam Name: Querying Microsoft SQL Server 2012
Updated: Jul 21, 2017
Q&As: 164
Choosing Microsoft 70-461 pdf study material means you choose an effective, smart, and fast way to succeed in your 070-461 pdf exam certification. You will find explanations along with the answers where is necessary in the 070-461 pdf actual test files.
Pass4itsureLatest and Most Accurate 70-461 PDF Dumps Exam Q&As:
Question No: 26You develop a Microsoft SQL Server 2012 database that contains a table named Products.
The Products table has the following definition: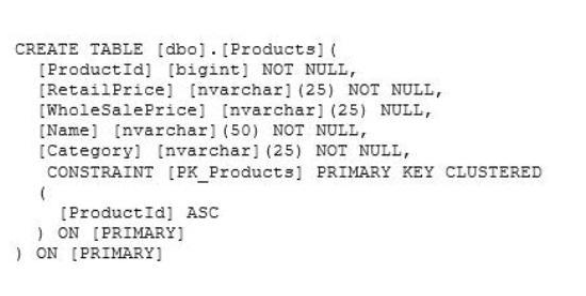
You need to create an audit record only when either the retail price or wholesale price
the column is updated.
Which Transact-SQL query should you use?
A. CREATE TRIGGER TrgPriceChange ON Products FOR UPDATE AS
IF CCLUMNS_CHANGED(retail price, wholesale price)
– – Create Audit Records
B. CREATE TRIGGER TrgPriceChange ON Products FOR UPDATE AS
IF EXISTS(SELECT RetailPrice from inserted) OR
EXISTS (SELECT WholeSalePnce FROM inserted)
– – Create Audit Records
C. CREATE TRIGGER TrgPriceChange ON Products FOR UPDATE AS
IF COLUMNS_UPDATED(retail price, wholesale price)
– – Create Audit Records
D. CREATE TRIGGER TrgPriceChange ON Products FOR UPDATE AS
IF UPDATE(retail price) OR UPDATE(wholesale price)
– – Create Audit Records
070-461 pdf Answer: D
Question No: 27A table named Profits stores the total profit made each year within a territory. The Profits
the table has columns named Territory, Year, and Profit.
You need to create a report that displays the profits made by each territory for each year
and its previous year.
Which Transact-SQL query should you use?
A. SELECT Territory, Year, Profit,
LEAD(Profit, 1, 0) OVER (PARTITION BY Territory ORDER BY Year) AS PrevProfit
FROM Profits
B. SELECT Territory, Year, Profit,
LAG(Profit, 1, 0) OVER (PARTITION BY Year ORDER BY Territory) AS PrevProfit
FROM Profits
C. SELECT Territory, Year, Profit,
LAG(Profit, 1, 0) OVER (PARTITION BY Territory ORDER BY Year) AS PrevProfit
FROM Profits
D. SELECT Territory, Year, Profit,
LEAD(Profit, 1, 0) OVER (PARTITION BY Year ORDER BY Territory) AS PrevProfit
FROM Profits
Answer: C
Question No: 28 You use Microsoft SQL Server 2012 database to develop a shopping cart application.
You need to rotate the unique values of the ProductName field of a table-valued expression
into multiple columns in the output.
Which Transact-SQL operator should you use?
A. CROSS JOIN
B. CROSS APPLY
C. PIVOT
D. UNPIVOT
070-461 exam Answer: C
Explanation:
Question No: 29 You administer a Microsoft SQL Server database that supports a shopping application.
You need to retrieve a list of customers who live in territories that do not have a salesperson. Which Transact- SQL query or queries should you use? (Each correct answer presents a
complete solution. Choose all that apply.)
A. SELECT CustomerID FROM Customer
WHERE TerritoryID <> SOME(SELECT TerritoryID FROM Salesperson)
B. SELECT CustomerID FROM Customer
WHERE TerritoryID <> ALL(SELECT TerritoryID FROM Salesperson)
C. SELECT CustomerID FROM Customer
WHERE TerritoryID <> ANY(SELECT TerritoryID FROM Salesperson)
D. SELECT CustomerID FROM Customer
WHERE TerritoryID NOT IN(SELECT TerritoryID FROM Salesperson) Answer: B, D
You support a database structure shown in the exhibit. (Click the Exhibit button.)
Question No: 30
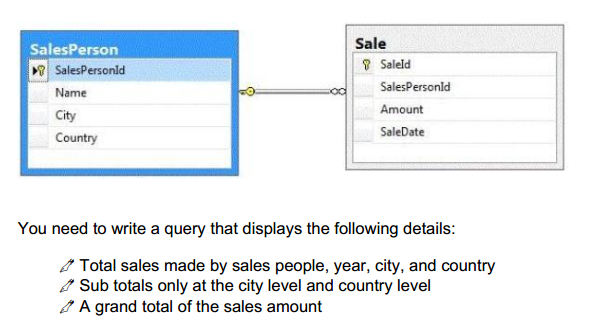
Which Transact-SQL query should you use?
A. SELECT SalesPerson.Name, Country, City,
DatePart(yyyy, SaleDate) AS Year, Sum(Amount) AS Total
FROM Sale INNER JOIN SalesPerson
ON Sale.SalesPersonID = SalesPerson.SalesPersonID
GROUP BY GROUPING SETS((SalesPerson.Name, Country, City, DatePart(yyyy,
SaleDate)), (Country, City), (Country), ())
B. SELECT SalesPerson.Name, Country, City,
DatePart(yyyy, SaleDate) AS Year, Sum(Amount) AS Total
FROM Sale INNER JOIN SalesPerson
ON Sale.SalesPersonID = SalesPerson.SalesPersonID
GROUP BY CUBE(SalesPerson.Name, Country, City, DatePart(yyyy, SaleDate))
C. SELECT SalesPerson.Name, Country, City,
DatePart(yyyy, SaleDate) AS Year, Sum(Amount) AS Total
FROM Sale INNER JOIN SalesPerson
ON Sale.SalesPersonID = SalesPerson.SalesPersonID
GROUP BY CUBE(SalesPerson.Name, DatePart(yyyy, SaleDate), City, Country)
D. SELECT SalesPerson.Name, Country, City,
DatePart(yyyy, SaleDate) AS Year, Sum(Amount) AS Total
FROM Sale INNER JOIN SalesPerson
ON Sale.SalesPersonID = SalesPerson.SalesPersonID
GROUP BY ROLLUP(SalesPerson.Name, DatePart(yyyy, SaleDate), City, Country)
070-461 dumps Answer: A
Explanation:
Be careful with this question, because on an exam can be different options for answer.
And none of them is correct : D You should report this question.
You are developing a database that will contain price information. You need to store the
prices that include a fixed precision and a scale of six digits. Which data type should you
use?
A. Float
B. Money
C. Small money
D. Numeric
Answer: D
Explanation:
Numeric is the only one in the list that can give a fixed precision and scale.
Question No: 31
You administer a Microsoft SQL Server database that supports a banking transaction
management application.
You need to retrieve a list of account holders who live in cities that do not have a branch
location.
Which Transact-SQL query or queries should you use? (Each correct answer presents a
Question No: 32
complete solution. Choose all that apply.)
A. SELECT AccountHolderID
FROM AccountHolder
WHERE CityID NOT IN (SELECT CityID FROM BranchMaster)
B. SELECT AccountHolderID
FROM AccountHolder
WHERE CityID <> ALL (SELECT CityID FROM BranchMaster)
C. SELECT AccountHolderlD
FROM AccountHolder
WHERE CityID <> SOME (SELECT CityID FROM BranchMaster)
D. SELECT AccountHolderID
FROM AccountHolder
WHERE CityID <> ANY (SELECT CityID FROM BranchMaster)
70-461 vce Answer: A, B
Explanation:
Verified the answers as correct.
You administer a Microsoft SQL Server 2012 database. The database contains a table
named Employee. Part of the Employee table is shown in the exhibit. (Click the Exhibit
button.)
Question No: 33
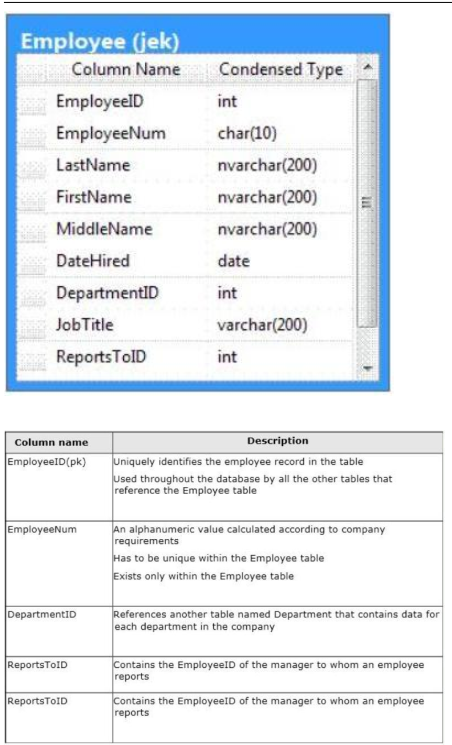
Confidential information about the employees is stored in a separate table named
employee data. One record exists within EmployeeData for each record in the Employee
table. You need to assign the appropriate constraints and table properties to ensure data
integrity and visibility. On which column in the Employee table should you create a unique
constraint?
A. DateHired
B. DepartmentID
C. employed
D. EmployeeNum
E. FirstName
F. JobTitle
G. LastName
H. MiddleName
I. ReportsToID
Answer: D
You administer a Microsoft SQL Server 2012 database. The database contains a table
named Employee. Part of the Employee table is shown in the exhibit. (Click the Exhibit
button.)
Question No: 34
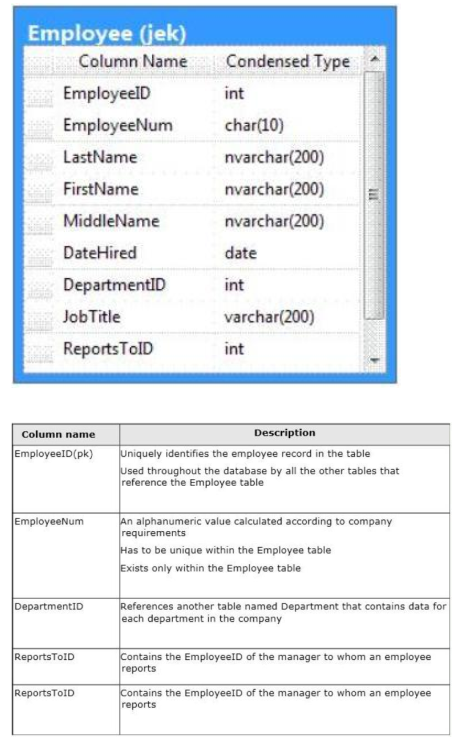
✑ ✑
Confidential information about the employees is stored in a separate table named
employee data. One record exists within EmployeeData for each record in the Employee
table.
You need to assign the appropriate constraints and table properties to ensure data integrity
and visibility.
On which column in the Employee table should you use an identity specification to include
a seed of 1,000 and an increment of 1?
A. DateHired
B. DepartmentID
C. EmployeeID
D. EmployeeNum
E. FirstName
F. JobTitle
G. LastName
H. MiddleName
I. ReportsToID
70-461 pdf Answer: C
You administer a Microsoft SQL Server 2012 database that includes a table named
Products. The Products table has columns named Productld, ProductName, and
CreatedDateTime.
The table contains a unique constraint on the combination of ProductName and
CreatedDateTime.
You need to modify the Products table to meet the following requirements:
Remove all duplicates of the Products table based on the ProductName column.
Retain only the newest Product row.
Which Transact-SQL query should you use?
A. WITH CTEDupRecords
AS
Question No : 35
SELECT MAX(CreatedDateTime) AS CreatedDateTime, ProductName
FROM Products
GROUP BY ProductName
HAVING COUNT(*) > 1
)
DELETE p
FROM Products p
JOIN CTEDupRecords cte ON
B. ProductName = cte.ProductName
AND p.CreatedDateTime > cte.CreatedDateTime
C. WITH CTEDupRecords
AS
(
SELECT MAX(CreatedDateTime) AS CreatedDateTime, ProductName
FROM Products
GROUP BY ProductName
HAVING COUNT(*) > 1
)
DELETE p
FROM Products p
JOIN CTEDupRecords cte ON
cte.ProductName = p.ProductName
AND cte.CreatedDateTime > p.CreatedDateTime
D. WITH CTEDupRecords
AS
(
SELECT MIN(CreatedDateTime) AS CreatedDateTime, ProductName
FROM Products
GROUP BY ProductName
)
DELETE p
FROM Products p
JOIN CTEDupRecords cte ON
E. ProductName = cte.ProductName
F. WITH CTEDupRecords
AS
(
SELECT MAX(CreatedDateTime) AS CreatedDateTime, ProductName
FROM Products
GROUP BY ProductName
HAVING COUNT(*) > 1
)
DELETE p
FROM Products p
JOIN CTEDupRecords cte ON
G. ProductName = cte.ProductName
Answer: B
Question No: 36You develop three Microsoft SQL Server 2012 databases named Database1, Database2,
and Database3.
You have permissions on both Database1 and Database2. You plan to write and deploy a
stored procedure named dbo.usp_InsertEvent in Database3. dbo.usp_InsertEvent must
execute other stored procedures in the other databases.
You need to ensure that callers that do not have permissions on Database1 or Database2
can execute the stored procedure.
Which Transact-SQL statement should you use?
A. USE Database2
B. EXECUTE AS OWNER
C. USE Database1
D. EXECUTE AS CALLER
070-461 dumps Answer: B
Question No: 37 You administer a Microsoft SQL Server 2012 database that has multiple tables in the Sales
schema. Some users must be prevented from deleting records in any of the tables in the
Sales schema. You need to manage users who are prevented from deleting records in the
Sales schema.
You need to achieve this goal by using the minimum amount of administrative effort. What
should you do? A. Create a custom database role that includes the users. Deny Delete permissions on the
Sales schema for the custom database role.
B. Include the Sales schema as an owned schema for the db_denydatawriter role. Add the
users to the
db_denydatawriter role.
C. Deny Delete permissions on each table in the Sales schema for each user.
D. Create a custom database role that includes the users. Deny Delete permissions on
each table in the Sales schema for the custom database role.
Answer: A
You administer a Microsoft SQL Server 2012 database. The database contains a Product
table created by using the following definition:
Question No: 38
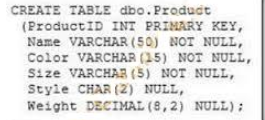
You need to ensure that the minimum amount of disk space is used to store the data in the
Product table.
What should you do?
A. Convert all indexes to Column Store indexes.
B. Implement Unicode Compression.
C. Implement row-level compression.
D. Implement page-level compression.
070-461 vce Answer: D
You generate a daily report according to the following query:
Question No: 39
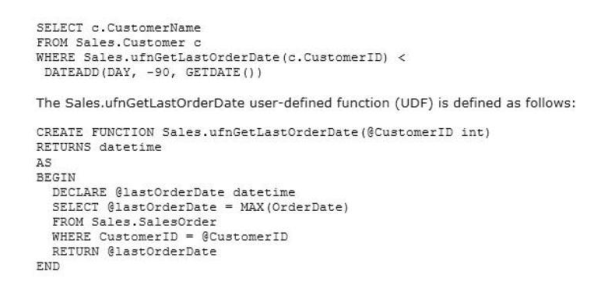
You need to improve the performance of the query.
What should you do?
A. Drop the UDF and rewrite the report query as follows:
WITH cte(CustomerID, LastOrderDate) AS (
SELECT CustomerID, MAX(OrderDate) AS [LastOrderDate]
FROM Sales.SalesOrder
GROUP BY CustomerID
)
SELECT c.CustomerName
FROM cte
INNER JOIN Sales.Customer c
ON cte.CustomerID = c.CustomerID
WHERE cte.LastOrderDate < DATEADD(DAY, -90, GETDATE())
B. Drop the UDF and rewrite the report query as follows:
SELECT c.CustomerName
FROM Sales.Customer c
WHERE NOT EXISTS (
SELECT s.OrderDate
FROM Sales.SalesOrder
WHERE s.OrderDate > DATEADD(DAY, -90, GETDATE())
AND s.CustomerID = c.CustomerID)
C. Drop the UDF and rewrite the report query as follows:
SELECT DISTINCT c.CustomerName
FROM Sales.Customer c
INNER JOIN Sales.SalesOrder s
ON c.CustomerID = s.CustomerID
WHERE s.OrderDate < DATEADD(DAY, -90, GETDATE())
D. Rewrite the report query as follows:
SELECT c.CustomerName
FROM Sales.Customer c
WHERE NOT EXISTS (SELECT OrderDate FROM
Sales.ufnGetRecentOrders(c.CustomerID,
90))
Rewrite the UDF as follows:
CREATE FUNCTION Sales.ufnGetRecentOrders(@CustomerID int, @MaxAge DateTime)
RETURNS TABLE AS RETURN (
SELECT OrderDate
FROM Sales.SalesOrder
WHERE s.CustomerID = @CustomerID
AND s.OrderDate > DATEADD(DAY, [email protected], GETDATE())
070-461 exam Answer: A
You administer a Microsoft SQL Server 2012 database named ContosoDb. Tables are
defined as shown in the exhibit. (Click the Exhibit button.)
Question No : 40
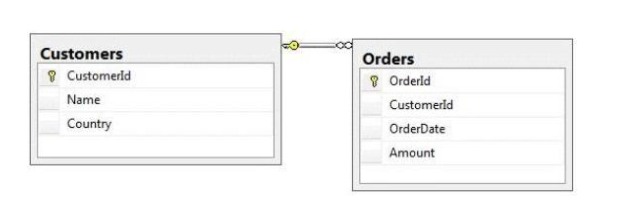
You need to display rows from the Orders table for the Customers row having the
CustomerId value set to 1 in the following XML format:
<row OrderId="1″ OrderDate="2000-01-01T00:00:00″ Amount="3400.00″
Name="Customer
A" Country="Australia" />
<row OrderId="2″ OrderDate="2001-01-01T00:00:00″ Amount="4300.00″
Name="Customer
A" Country="Australia" />
Which Transact-SQL query should you use?
A. SELECT OrderId, OrderDate, Amount, Name, Country
FROM Orders INNER JOIN Customers ON Orders.CustomerId = Customers.CustomerId
WHERE Customers.CustomerId = 1
FOR XML RAW
B. SELECT OrderId, OrderDate, Amount, Name, Country
FROM Orders INNER JOIN Customers ON Orders.CustomerId = Customers.CustomerId
WHERE Customers.CustomerId = 1
FOR XML RAW, ELEMENTS
C. SELECT OrderId, OrderDate, Amount, Name, Country
FROM Orders INNER JOIN Customers ON Orders.CustomerId = Customers.CustomerId
WHERE Customers.CustomerId = 1
FOR XML AUTO
D. SELECT OrderId, OrderDate, Amount, Name, Country
FROM Orders INNER JOIN Customers ON Orders.CustomerId – Customers.CustomerId
WHERE Customers.CustomerId= 1
FOR XML AUTO, ELEMENTS
E. SELECT Name, Country, OrderId, OrderDate, Amount
FROM Orders INNER JOIN Customers ON Orders.CustomerId= Customers.CustomerId
WHERE Customers.CustomerId- 1
FOR XML AUTO
F. SELECT Name, Country, Ordered, OrderDate, Amount
FROM Orders INNER JOIN Customers ON Orders.CustomerId= Customers.CustomerId
WHERE Customers.CustomerId= 1
FOR XML AUTO, ELEMENTS
G. SELECT Name AS '@Name', Country AS '@Country', OrderId, OrderDate, Amount
FROM Orders INNER JOIN Customers ON Orders.CustomerId= Customers.CustomerId
WHERE Customers.CustomerId= 1
FOR XML PATH ('Customers')
H. SELECT Name AS 'Customers/Name', Country AS 'Customers/Country', OrderId,
OrderDate, Amount
FROM Orders INNER JOIN Customers ON Orders.CustomerId= Customers.CustomerId
WHERE Customers.CustomerId= 1
FOR XML PATH ('Customers')
Answer: A
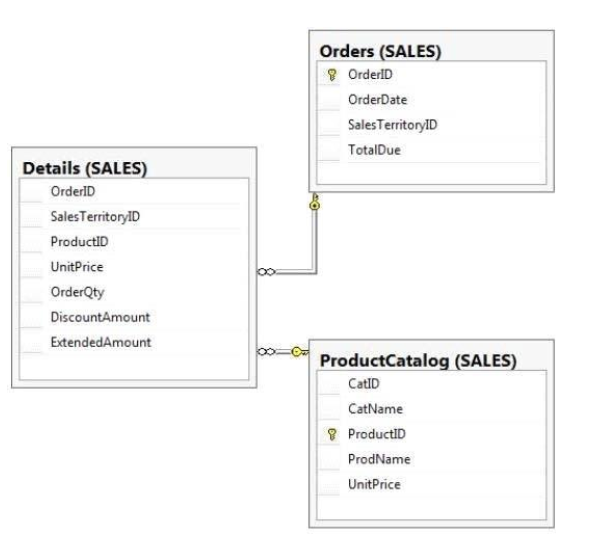
You have a database that contains the tables as shown in the exhibit. (Click the Exhibit
button.)
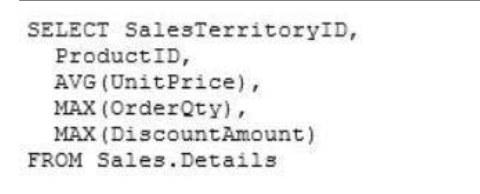
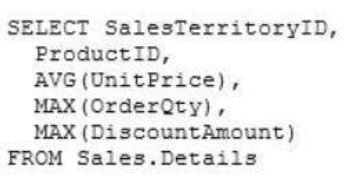
Question No: 41 CORRECT TEXT
You have the following query:
✑ ✑ ✑ ✑
You need to recreate the query to meet the following requirements:
Reference columns by using one-part names only.
Sort aggregates by SalesTerritoryID, and then by ProductID.
Order the results in descending order from SalesTerritoryID to Product
The solution must use the existing SELECT clause and FROM clause
Which code segment should you use?
To answer, type the correct code in the answer area.
Answer: Please review the explanation part for this answer
Answer:
With the study by the Pass4itsure 070-461 pdf, you will have a clear understanding of the 070-461 pdf valid dumps. In addition, you can print the 070-461 pdf dumps into papers, thus you can do marks on the papers. Every time, when you review the papers, you will enhance your memory about the marked points. Be confident to attend your 070-461 pdf exam test, you will pass successfully.
The Microsoft Certification website and this preparation guide contain a variety of resources to help you prepare for an exam. Preparing for and taking a Pass4itsure https://www.pass4itsure.com/70-461.html pdf exam — FAQ provides answers to frequently asked questions about exam registration, preparation, scoring, and policies, including google drive: https://drive.google.com/open?id=0BwxjZr-ZDwwWRFNLVl8xNFJPejg
Is going for the brain dumps for Microsoft 070-413 dumps the right way? "Designing and Implementing a Server Infrastructure" is the name of Microsoft 070-413 exam dumps which covers all the knowledge points of the real Microsoft exam. Best Pass4itsure Microsoft 070-413 dumps exam study guide Designing and Implementing a Server Infrastructure. Pass4itsure Microsoft 070-413 dumps exam questions answers are updated (245 Q&As) are verified by experts.
The associated certifications of 070-413 dumps is Microsoft Server Infrastructure. Pass4itsure can 100% guarantee you to pass the exam, if you fail to pass the https://www.pass4itsure.com/70-413.html dumps exam, we will full refund to you.
Exam Code: 70-413
Exam Name: Designing and Implementing a Server Infrastructure
Q&As: 245
[Ensure Pass Microsoft 70-413 DumpsExam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWYkpNOFdaS1QtcUE
[Ensure Pass Microsoft 70-463 Dumps Exam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWSHdVQTJwd19hV3c
Latest and Most Accurate Pass4itsure 070-413 Dumps Exam Q&As:
QUESTION NO: 31
Adam works as a professional Penetration tester. A project has been assigned to him to employ penetration testing on the network of Umbrella Inc. He is running the test from home and had downloaded every security scanner from the Internet. Despite knowing the IP range of all of the systems, and the exact network configuration, Adam is unable to get any useful results. Which of the following is the most like cause of this problem?
Each correct answer represents a complete solution. Choose all that apply.
A. Security scanners are only as smart as their database and cannot find unpublished vulnerabilities.
B. Security scanners cannot perform vulnerability linkage.
C. Security scanners are smart as their database and can find unpublished vulnerabilities.
D. Security scanners are not designed to do testing through a firewall.
070-413 exam Answer: A,B,D
QUESTION NO: 32
An organization monitors the hard disks of its employees' computers from time to time. Which policy does this pertain to?
A. Network security policy
B. User password policy
C. Privacy policy
D. Backup policy
Answer: C
QUESTION NO: 33
You work as a Network Administrator for Net World International. You have configured the hard disk drive of your computer as shown in the image below: The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?
A. The file is corrupt.
B. The 6GB partition is corrupt.
C. Windows 98 does not support the NTFS file system.
D. Files saved in Windows 98 are not supported by Windows 2000.
070-413 dumps Answer: C
QUESTION NO: 34
Peter works as a Computer Hacking Forensic Investigator. He has been called by an organization to conduct a seminar to give necessary information related to sexual harassment within the workplace. Peter started with the definition and types of sexual harassment. He then wants to convey that it is important that records of the sexual harassment incidents should be maintained, which helps in further legal prosecution. Which of the following data should be recorded in this documentation?
Each correct answer represents a complete solution. Choose all that apply.
A. Names of the victims
B. Date and time of incident
C. Nature of harassment
D. Location of each incident
Answer: A,B,D
QUESTION NO: 35
Which of the following types of computers is used for attracting potential intruders?
A. Bastion host
B. Data pot
C. Files pot
D. Honey pot
070-413 pdf Answer: D
QUESTION NO: 36
Which of the following standard file formats is used by Apple's iPod to store contact information?
A. HFS+
B. hCard
C. vCard
D. FAT32
Answer: C
QUESTION NO: 37
Which of the following file systems cannot be used to install an operating system on the hard disk drive? Each correct answer represents a complete solution. Choose two.
A. Windows NT file system (NTFS)
B. High-Performance File System (HPFS)
C. Log-structured file system (LFS)
D. Compact Disc File System (CDFS)
E. Novell Storage Services (NSS)
070-413 vce Answer: C,D
QUESTION NO: 38
Which of the following types of evidence proves or disproves a specific act through oral testimony based on information gathered through the witness's five senses?
A. Conclusive evidence
B. Best evidence
C. Hearsay evidence
D. Direct evidence
Answer: D
QUESTION NO: 39
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
A. Digital certificates
B. Public key
C. RSA
D. Twofish
070-413 exam Answer: A,B
QUESTION NO: 40
Which of the following sections of an investigative report covers the background and summary of the report including the outcome of the case and the list of allegations?
A. Section 2
B. Section 4
C. Section 3
D. Section 1
Answer: A
QUESTION NO: 41
Which of the following switches of the XCOPY command copies attributes while copying files?
A. /o
B. /p
C. /k
D. /s
070-413 dumps Answer: D
QUESTION NO: 42
Which of the following directories in Linux operating system contains device files, which refers to physical devices?
A. /boot
B. /etc
C. /dev
D. /bin
Answer: C
QUESTION NO: 43
Which of the following directories cannot be placed out of the root filesystem? Each correct answer represents a complete solution. Choose all that apply.
A. /sbin
B. /etc
C. /var
D. /lib
070-413 pdf Answer: A,B,D
QUESTION NO: 44
On which of the following locations does the Windows NT/2000 operating system contain the SAM, SAM.LOG, SECURITY.LOG, APPLICATION.LOG, and EVENT.LOG files?
A. \%Systemroot%system32
B. \%Systemroot%profiles
C. \%Systemroot%system32config
D. \%Systemroot%help
Answer: C
QUESTION NO: 45
You are handling technical support calls for an insurance company. A user calls you complaining that he cannot open a file, and that the file name appears in green while opening in Windows Explorer.
What does this mean?
A. The file is encrypted.
B. The file belongs to another user.
C. The file is infected with virus.
D. The file is compressed.
070-413 vce Answer: A
QUESTION NO: 46
Which of the following is a name, symbol, or slogan with which a product is identified?
A. Trade secret
B. Patent
C. Copyright
D. Trademark
Answer: D
QUESTION NO: 47
Which of the following file systems supports the hot fixing feature?
A. FAT16
B. exFAT
C. FAT32
D. NTFS
070-413 exam Answer: D
Pass4itsure 070-413 dumps original exercises is very similar with real exam questions. If you choose Pass4itsure's testing practice questions and answers, we will provide you with a year of free https://www.pass4itsure.com/70-413.html dumps online update service.
Read More Youtube:https://youtu.be/dWNX36UZdOM
Microsoft 70-489 dumps is a Microsoft certification exam and IT professionals who have passed some Microsoft certification exams are popular in IT industry. Pass4itsure guide new updated MCSD exam https://www.pass4itsure.com/70-489.html dumps exam with latest version pdf&vce.
Exam Code: 70-489
Exam Name: Developing Microsoft SharePoint Server 2013 Advanced Solutions
Updated: Aug 10, 2017
Q&As: 97
[Ensure Pass Microsoft 70-489 Dumps Exam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWMVJwQXUxZ0JQV28
[Ensure Pass Cisco 200-355 Dumps Exam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWUkUwT0lYclNxbFU
So more and more people participate in Microsoft 070-489 dumps, but 70-489 certification exam is not very simple.

Pass4itsure Latest and Most Accurate 70-489 Dumps Exam Q&As:
1. Which GVP software component is used to configure the various components of GVP including
application provisioning?
A. Element Management Provisioning System
B. IP Call Manager
C. Voice Application Reporter
D. Genesys Studio
070-489 exam Answer: A
2. Which GVP application is used to build and test voice applications?
A. Element Management Provisioning System
B. IP Call Manager
C. Voice Application Reporter
D. Genesys Studio
Answer: D
3. Which version of the VoiceXML Specification does GVP version 7.5 support?
A. VoiceXML 1.0
B. VoiceXML 1.1
C. VoiceXML 2.0
D. VoiceXML 3.0
070-489 dumps Answer: C
4. The GVP VoiceXML application logic resides on .
A. a web server
B. the VCS
C. the VPM
D. the IPCM
Answer: A
5. How are VoiceXML pages produced during a GVP call session?
A. Web application server generates VoiceXML when processing asp or jsp pages
B. VCS or IPCS produce VoiceXML when the call is initiated
C. EMPS produces VoiceXML when the request comes in
D. IPCS creates the VoiceXML when it relays SIP messages
070-489 pdf Answer: A
6. The Voice Communication Server (VCS) processes calls.
A. VoIP
B. IPCS
C. Web-based GUI
D. TDM
Answer: D
7. The Internet Protocol Communication Server (IPCS) processes calls.
A. SIP
B. HTML
C. TDM D.
EMPS
070-489 vce Answer: A
8. The Internet Protocol Communication Server (IPCS) processes calls.
A. SIP
B. HTML
C. TDM D.
EMPS
Answer: A
9. A Primary Voice Application URL is required when provisioning the IVR Profile. The Primary Voice
Application CANNOT include .
A. the fully qualified name of the web server that hosts the application
B. the numeric IP address of the web server that hosts the application
C. the name of the first page of the voice application
D. the path to the <Application Name>.XML file
070-489 exam Answer: D
10. Refer to the CTI Property tab in the Provisioning IVR profile section in the EMPS. The Default Route
Number is used when .
A. IVR Server is unable to contact the Solution Control Interface (SCI)
B. IVR Server is unable to contact the Universal Routing Server (URS), or when the URS is unable to
find an agent number to which it can route the call
C. IVR component, specifically Genesys Queue Adapter (GQA), cannot communicate with SCS.
D. IVR Server component cannot communicate with the Web Server
Answer: B
11.The <DNIS>.XML and <Application_Name>.xml files are generated when .
A. a call arrives at the VCS
B. an application is created and configured in EMPS
C. the WatchDog on the EMPS is restarted
D. requested by the IVR Server
070-489 dumps Answer: B
12. The <Application_Name>.xml files provides all of the .
A. VCS configuration information
B. voice application information
C. IPCS configuration information
D. web server configuration information
Answer: B
13. The DNIS.xml provides . A. the Primary Application URL
B. all application configuration information but no process information
C. the address of the IVR Server
D. the URL path to the <Application_Name>.XML
070-489 pdf Answer: D
14. Where is the default location of the DNIS Application Mapping Files?
A. <install dir>\CN\data
B. <install dir>\CN\web\dispenser\spd_data
C. <install dir>\CN\config
D. http://EMPS:9810/spm
Answer: B
15. In the <Application_Name>.xml file, the IVRTimeout value determines .
A. how long URS waits for the response from web server before timing out and trying default routing
target.
B. how long VCS/IPCS waits for the response from web server before timing out and attempting to reach
the Backup IVR URL.
C. how long GQA waits for the connection with the IVR Server before using the Backup IVR URL.
D. how long VCS/IPCS waits for the response from web server before timing out and attempting to reach
the Primary IVR URL.
070-489 vce Answer: B
16. Which of the following features can be changed using the Element Management System (EMS) GUI
when monitoring a VCS?
A. the log level for each process
B. the default directory for logging
C. the Behind or In-Front configuration for that particular VCS
D. the speech recognition vendor for that particular VCS
Answer: A
17.When would you use the Import Server Instance CSV feature in EMPS?
A. Never. This feature is not available through the EMPS
B. Any time you want to make a change to any of the parameters in EMPS
C. You want to start the Watchdog service
D. When numerous changes are needed with servers or configuration of various components for a
server and in conjunction with Genesys Technical Support
070-489 exam Answer: D
18. Under what circumstances is a username and password required to access the EMPS?
A. Never. By default, a username and password is not required since EMPS is only used for monitoring
purposes.
B. Always. When opening EMPS Login screen, the system will require users enter their username and
password.
C. Only when the EMPS is being accessed from a remote workstation. You are automatically
authenticated and can log in from a local machine.
D. Only when using SunOne Directory Server because OpenLDAP has no built-in security for the EMPS
login screen.
Answer: B
19. The ability to record the caller's speech for application analysis is configured in an IVR Profile within
the EMPS and is referred to as .
A. OA&M
B. EMS Runtime
C. Enable ASR Transcoding
D. Enable ASR Logging
070-489 dumps Answer: D
20.The process on the VCS/IPCS that starts the other component processes is the .
A. Page Collector
B. IVR Server Client C.
Call Flow Assistant D.
WatchDog
Answer: D
21.Which VCS/IPCS component controls the TDM telephony or IP Telephony interfaces?
A. PopGateway
B. Page Collector
C. MRCP Client
D. Net Management
070-489 pdf Answer: A
22. Which of the following are Windows prerequisites for VCS?
A. there are no Windows prerequisites
B. Active Directory
C. IIS and SNMP
D. SQL Server
Answer: C
23. A logical group of ports is referred to as a .
A. Telephony Manager
B. Route
C. Page Collector
D. MRCP Client
070-489 vce Answer: B
24. For most deployments with VCS configured in Behind-the-Switch mode using Genesys Framework,
DNIS is obtained through what mechanism?
A. VCS request to the T-Server via IVR Server
B. VCS requests to the Dialogic telephony board
C. a route point corresponding to the appropriate strategy
D. VCS request directly to the ACD/PBX
Answer: A
If you do not have participated in a professional specialized training course, you need to spend a lot of time and effort to prepare for the Microsoft 070-489 dumps exam. But now Pass4itsure can help you save a lot of your precious time and energy: https://www.pass4itsure.com/70-489.html
Do you have feedback about the relevance of the skills measured on this 70-480 exam? Please send Microsoft your comments. All feedback will be reviewed and incorporated as appropriate while still maintaining the validity and reliability of the certification process. Note that Microsoft will not respond directly to your feedback. Testcos appreciate your input in ensuring the quality of the Microsoft Certification program.
Vendor: Microsoft
Certifications: Microsoft Windows Store apps
Exam Name: Programming in HTML5 with JavaScript and CSS3
Exam Code: 70-480
Total Questions: 205 Q&As
Last Updated: Mar 06, 2017
Exam Information:https://www.pass4itsure.com/70-480.html

"Dear User,
Thanks for contacting us. In the 70-480 vceexam description, you will be taken thru a series of steps to identify the exam and the center where you want the exam and on the final page where the you are supposed to click on commit registration. Click the link and in the popup that opens he should select discount type as promotion code and enter HTMLJMP as value and click on validate. This will apply the discount on the total fee of the exam.
Please let me know if you have any other questions.
Regards,
testcos.com"
Share some Microsoft Specialist 70-480 Exam Questions and Answers Below:
Question No : 18 HOTSPOT – (Topic 1)An HTML page has a canvas element.
You need to draw a red rectangle on the canvas element dynamically. The rectangle
should resemble the following graphic.

How should you build the code segment? (To answer, select the appropriate options from
the drop-down lists in the answer area.)



Question No : 19 – (Topic 1)You are developing an HTML5 page that has an element with an ID of logo. The page
includes the following HTML.
<div>
Logo:<br>
<div id="logo">
</div>
</div>
You need to move the logo element lower on the page by five pixels.
Which lines of code should you use? (Each correct answer presents part of the solution.
Choose two.)
A. document.getElementById("logo") .style.position = "relative";
B. document.getElementByld("logo").Style.top = "5px";
C. document.getElementById("logo").style.top = "-5px";
D. document.getElementById("logo").style.position = "absolute";
Answer: A,B
Reference:
Question No : 20 – (Topic 1)You are developing a web page by using HTML5 and C5S3. The page includes a <div> tag
with the ID set to validate.
When the page is rendered, the contents of the <div> tag appear on a line separate from
the content above and below it. The rendered page resembles the following graphic.

The page must be rendered so that the <div> tag is not forced to be separate from the
other content. The following graphic shows the correctly rendered output.

You need to ensure that the page is rendered to meet the requirement.
Which line of code should you use?
A. document.getElementById("validate").style.display = "inline";
B. document.getElementById("validate").style.margin = "0";
C. document.getElementById("validate").style.padding = "0";
D. document.getElementSyId("validate").style.display = "block";
Answer: A
Reference:
Question No : 21 HOTSPOT – (Topic 1) You are creating a web worker for an HTML5 application.
The following tasks must be performed from within the web worker:
Register an event listener for the web worker
Start and stop the web worker
You need to define a function that performs the required tasks.
Which code segment should you use? (To answer, select the appropriate option from the
drop-down list in the answer area.)



Question No : 22 – (Topic 1)You are creating a JavaScript function that displays the name of a web application.
You declare the following button element.
<input type="button" id= "About" value="About" />
When a user clicks the button, a JavaScript function named About must be called.
You need to create an event handler that calls the About function when the button is
clicked.
Which two code segments can you use? (Each correct answer presents a complete
solution. Choose two.)

A. Option A
B. Option B
C. Option C
D. Option D
Answer: C,D
Reference:
Question No : 23 HOTSPOT – (Topic 1)You are creating a function by using JavaScript. The function accepts an object as the
parameter and returns a string that identifies the data type of the object.
✑ ✑ ✑
You have the following requirements:
The function must return "Number" if the object is a number.
The function must return "String" if the object is a string.
The function must return "Unknown" if the object is neither a number nor a string.
You need to implement the function to meet the requirements.
How should you build the code segment? (To answer, select the appropriate options from
the drop-down lists in the answer area.)



Question No : 24 – (Topic 1)You need to test the value of the following variable in JavaScript.
var length = "75";
A block of code must execute if the length equals 75 regardless of the data type.
You need to use the statement that meets this requirement.
Which lines of code should you use? (Each correct answer presents a complete solution.
Choose two.)
A. if (length = = = 75)
B. if (length = = 75)
C. if (length! = 75)
D. if (length = = "75")
Answer: B,D
Question No : 25 – (Topic 1) You are developing an application that uses a third-party JavaScript library named
doWork().
The library occasionally throws an "object is null or undefined" error with an error code of
-2146823281.
The application must:
Extract and handle the exceptions thrown by doWork()
Continue normal program execution if other exceptions occur
You need to implement the requirements.
Which code segment should you use?

A. Option A
B. Option B
C. Option C
D. Option D
Answer: C
I'll keep things short and sweet in this 70-480 vce . The content below will cover all of the sections described in the "Skills Measured" section of the Microsoft article that describes the Microsoft Certification exam 70-480 dumps: Programming in HTML5 with JavaScript and CSS3. I was not surprised to find that the vast majority of the test topics are discussed on the following two sites: https://www.collection4pdf.com/microsoft-70-483-exam-certification-training/, and https://www.exampass.net/microsoft-70-243-exam-youtube-training-materials.html. Since all three of these sites provide extremely reliable information, I attempted to stick with these three sites for all of the 70-480 pdf study guide materials. You will find that for the most part I was successful. Enough of my rambling though. Let's get started.
Exam Code: 70-411
Exam Name: Administering Windows Server 2012
Updated: Mar 17, 2017
Q&As: 234
Published: September 17, 2012
Languages: English, Chinese (Simplified), French, German, Japanese, Portuguese (Brazil)
Audiences:IT professionals
Technology: Windows Server 2012 R2
Credit toward certification: MCP, MCSA, MCSE
Exam Information:https://www.pass4itsure.com/70-411.html
70-411Exam Objetives
1.1 Deploy and manage server images
- Windows Deployment Services Overview (TechNet Library)

- What's New for Windows Deployment Services (TechNet Library)
- Windows Deployment Services Getting Started Guide for Windows Server 2012 (TechNet Library)
- Deploying 70-411 examWindows Server 2012: From Bare Metal, Server Core, Minimal Server Interface, and More (Session: Andrew Mason @ TechEd North America 2012)
- What's New in Windows Deployment Services in Windows Server 2012 R2 (R2)
- Windows Deployment Services Cmdlets in Windows PowerShell (R2)
- Using the WDS PowerShell Cmdlets in Windows Server 2012 R2 (R2)
- Managing and Deploying Driver Packages in Windows Deployment Services (R2)
Real4exam Latest and Most Accurate Microsoft70-411 Exam Q&As
70-411 exam Question No : 32 – (Topic 0)Your network contains an Active Directory domain named contoso.com. The domain
contains a file server named Server1 that runs Windows Server 2012 R2. Server1 has a
share named Share1.
When users without permission to Share1 attempt to access the share, they receive the
Access Denied message as shown in the exhibit. (Click the Exhibit button.)
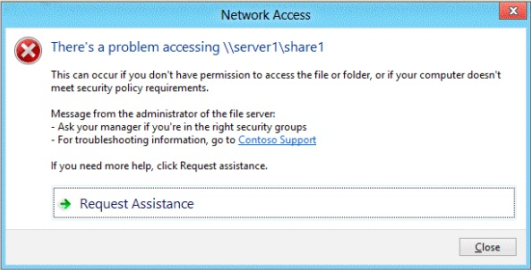
You deploy a new file server named Server2 that runs Windows Server 2012 R2.
You need to configure Server2 to display the same custom Access Denied message as
Server1.
What should you install on Server2?
A. The Remote Assistance feature
B. The Storage Services server role
C. The File Server Resource Manager role service
D. The Enhanced Storage feature
Answer: C
Explanation:
Access-Denied Assistance is a new role service of the File Server role in Windows Server
2012.
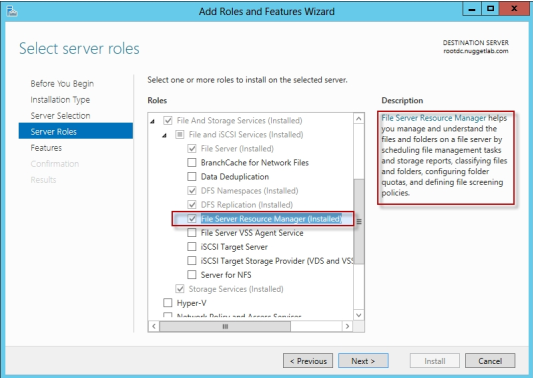
We need to install the prerequisites for Access-Denied Assistance.
Because Access-Denied Assistance relies up on e-mail notifications, we also need to
configure each relevant file server with a Simple Mail Transfer Protocol (SMTP) server
address. Let's do that quickly with Windows PowerShell:
Set-FSRMSetting -SMTPServer mailserver. nuggetlab.com -AdminEmailAddress
[email protected] -FromEmailAddress [email protected]
You can enable Access-Denied Assistance either on a per-server basis or centrally via
Group Policy. To my mind, the latter approach is infinitely preferable from an administration
standpoint.
Create a new GPO and make sure to target the GPO at your file servers' Active Directory
computer accounts as well as those of your AD client computers. In the Group Policy
Object Editor, we are looking for the following path to configure Access-Denied Assistance:
\Computer Configuration\Policies\Administrative Templates\System\Access-Denied
Assistance
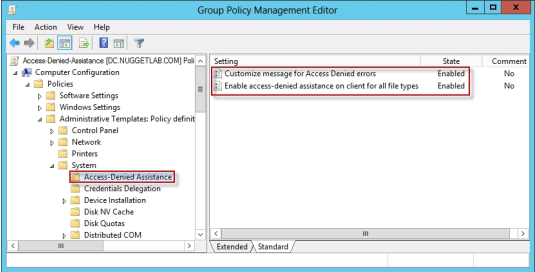
The Customize message for Access Denied errors policy, shown in the screenshot below,
enables us to create the actual message box shown to users when they access a shared
file to which their user account has no access.
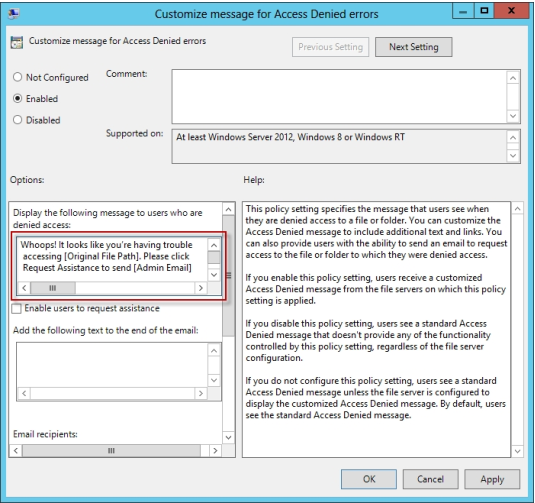
What's cool about this policy is that we can "personalize" the e-mail notifications to give us
administrators (and, optionally, file owners) the details they need to resolve the permissions
issue quickly and easily.
For instance, we can insert pre-defined macros to swap in the full path to the target file, the
administrator e-mail address, and so forth. See this example:
Whoops! It looks like you're having trouble accessing [Original File Path]. Please click
Request Assistance to send [Admin Email] a help request e-mail message. Thanks!
You should find that your users prefer these human-readable, informative error messages
to the cryptic, non-descript error dialogs they are accustomed to dealing with.
The Enable access-denied assistance on client for all file types policy should be enabled to
force client computers to participate in Access-Denied Assistance. Again, you must make
sure to target your GPO scope accordingly to "hit" your domain workstations as well as
your Windows Server 2012 file servers.
Testing the configuration
This should come as no surprise to you, but Access-Denied Assistance works only with
Windows Server 2012 and Windows 8 computers. More specifically, you must enable the
Desktop Experience feature on your servers to see Access-Denied Assistance messages
on server computers.
When a Windows 8 client computer attempts to open a file to which the user has no
access, the custom Access-Denied Assistance message should appear:
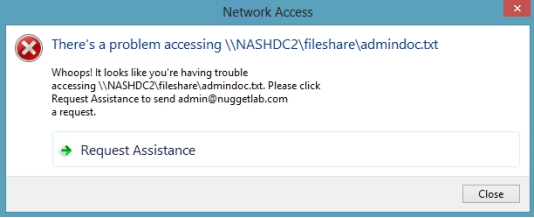
If the user clicks Request Assistance in the Network Access dialog box, they see a
secondary message:
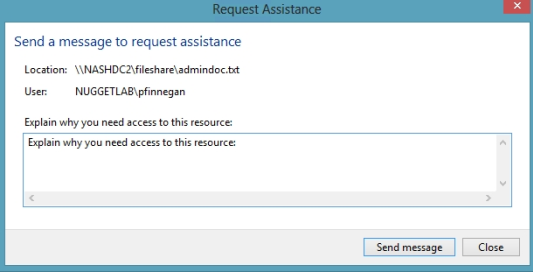
At the end of this process, the administrator(s) will receive an e-mail message that contains
the key information they need in order to resolve the access problem:
The user's Active Directory identity
The full path to the problematic file
A user-generated explanation of the problem
So that's it, friends! Access-Denied Assistance presents Windows systems administrators
with an easy-to-manage method for more efficiently resolving user access problems on
shared file system resources. Of course, the key caveat is that your file servers must run
Windows Server 2012 and your client devices must run Windows 8, but other than that, this
is a great technology that should save admins extra work and end-users extra headaches.
70-411 exam Question No : 33 – (Topic 0)You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the
File Server Resource Manager role service installed.
Each time a user receives an access-denied message after attempting to access a folder
✑ ✑ ✑ ✑ ✑ ✑ ✑
on Server1, an email notification is sent to a distribution list named DL1.
You create a folder named Folder1 on Server1, and then you configure custom NTFS
permissions for Folder1.
You need to ensure that when a user receives an access-denied message while attempting
to access Folder1, an email notification is sent to a distribution list named DL2. The
solution must not prevent DL1 from receiving notifications about other access-denied
messages.
What should you do?
A. From Server Manager, run the New Share Wizard to create a share for Folder1 by
selecting the SMB Share – Advanced option.
B. From the File Server Resource Manager console, modify the Access-Denied Assistance
settings.
C. From the File Server Resource Manager console, modify the Email Notifications
settings.
D. From Server Manager, run the New Share Wizard to create a share for Folder1 by
selecting the SMB Share -Applications option.
Answer: C
Explanation:
Configure the email notification settings
You must configure the email notification settings on each file server that will send the
access-denied assistance messages.
Open File Server Resource Manager. In Server Manager, click Tools, and then
click File Server Resource Manager.
Right-click File Server Resource Manager (Local), and then click Configure
Options.
Click the Email Notifications tab.
Configure the following settings:
In the SMTP server name or IP address box, type the name of IP address of the
SMTP server in your organization.
In the Default administrator recipients and Default "From" e-mail address boxes,
type the email address of the file server administrator.
Click Send Test E-mail to ensure that the email notifications are configured
correctly.
Click OK.
70-411 examQuestion No : 34 HOTSPOT – (Topic 0) Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2012 R2. Server1 has the File
Server Resource Manager role service installed.
You need to configure Server1 to meet the following requirements:
Ensure that old files in a folder named Folder1 are archived automatically to a
folder named Archive1.
Ensure that all storage reports are saved to a network share.
Which two nodes should you configure?
To answer, select the appropriate two nodes in the answer area.
70-411 exam Question No : 35 DRAG DROP – (Topic 0)You are a network administrator of an Active Directory domain named contoso.com.
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the
Web Server (IIS) server role installed.
Server1 will host a web site at URL The application pool
identity account of the web site will be set to a domain user account named AppPool1.
You need to identify the setspn.exe command that you must run to configure the
appropriate Service Principal Name (SPN) for the web site.
What should you run?
To answer, drag the appropriate objects to the correct location. Each object may be used
once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.
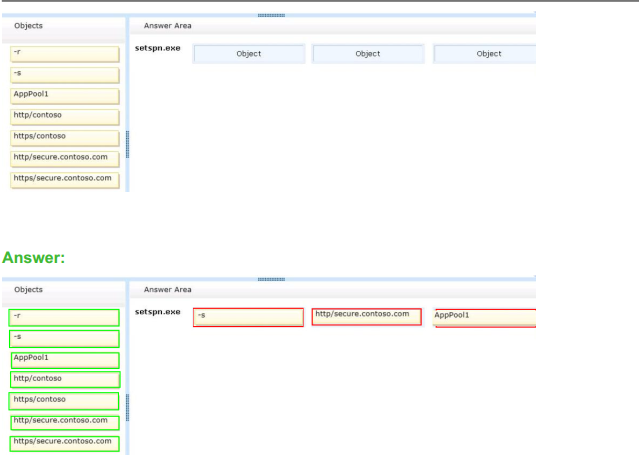
70-411 exam Question No : 36 – (Topic 0)Your network contains an Active Directory domain named contoso.com. The domain
contains a domain controller named DC1 that runs Windows Server 2012 R2. DC1 is
backed up daily.
The domain has the Active Directory Recycle Bin enabled.
During routine maintenance, you delete 500 inactive user accounts and 100 inactive
groups. One of the deleted groups is named Group1. Some of the deleted user accounts
are members of some of the deleted groups.
For documentation purposes, you must provide a list of the members of Group1 before the
group was deleted.
You need to identify the names of the users who were members of Group1 prior to its
deletion.
You want to achieve this goal by using the minimum amount of administrative effort. What should you do first?
A. Mount the most recent Active Directory backup.
B. Reactivate the tombstone of Group1.
C. Perform an authoritative restore of Group1.
D. Use the Recycle Bin to restore Group1.
Answer: A
Explanation:
The Active Directory Recycle Bin does not have the ability to track simple changes to
objects.
If the object itself is not deleted, no element is moved to the Recycle Bin for possible
recovery in the future. In other words, there is no rollback capacity for changes to object
properties, or, in other words, to the values of these properties.

Free Download New 70-411 exam Dumps: Real4exam now supplying the new version of 70-411 VCE dumps, we ensure our 447q 70-411 exam questions are the most authoritative and valid compared with others', which will ensure your 70-411 exam 100% passing, and now we are offering the free new version VCE simulator along with the VCE format 447q 70-411 braindumps, also the PDF format 70-411 exam is available now, welcome to choose.
Strongly Recommended:https://www.examinationsite.com/popular-mcsa-microsoft-70-411-exam/
The pass4itsure is an reliable and trustworthy platform who provides latest exam questions of Cisco, Microsoft, CompTIA, IBM, HP, Oracle, Citrix with 100% success guarantee.
Recommended Hottest Microsoft IT Certification Exam:
Pass4isture Microsoft is credited with having established various different certification systems. Each of those certifications is for a specific area of IT expertise. Certifications such as these help establish the knowledge credentials of an IT professionals. Among others, it serves two major functions:
- It helps an individual gauge his/her own level of knowledge and expertise
- It helps potential employers in finding the right candidates for the various IT positions
Pass4itsure.com provide our candidates with the latest exam materials updates for Microsoft. To ensure about the relevance and accuracy of our resources, the study materials are constantly revised and updated by our expert team. We guarantee the materials with quality and reliability which will help you pass any Microsoft certification exam.
We guarantee the materials with quality and reliability which will help you pass any Microsoft certification exam. When you take Microsoft exam, you can visit Pass4itsure to know the latest messages.
The Latest Pass4itsure Microsoft Dumps List:
The Latest Pass4itsure Cisco Dumps List:
Every year there are more than 35803+ candidates choosing pass4itsure. Our passing rate is high up to 98%.
Hot Microsoft Exam Questions Demo Samples:
2018 New Pass4isture Microsoft 70-341 Dumps Version: Candidates for this exam are senior administrators who act as the technical lead over a team of administrators. Candidates serve as a third level of support between the Exchange Recipient Administrator and the Exchange Server Administrator. Candidates should have a minimum of three years of experience managing Exchange servers and Exchange messaging in an enterprise environment.
QUESTION 1
You have an Exchange Server 2013 organization named adatum.com. The organization contains five Mailbox servers and two Client Access servers. You need to ensure that an administrator named user1 receives a daily email message that contains a log of all the Exchange Server administrative actions. Which cmdlet should you use in a scheduled task?
A. Search-AdminAuditLog
B. Set-Mailbox
C. New-AdminAuditLogSearch
D. Set-ExchangeServer
E. Set-AdminAuditLogConfig
Correct Answer: C
QUESTION 2
You have an Exchange Server 2013 organization named Contoso. The organization contains a server named Server1 that has Exchange Server 2013 installed. Server1 has the Mailbox server role and the Client Access server role installed. Server1 has a Send connector for a partner company. The Send connector is configured for Domain Security with a domain named adatum.com.
The only certificate installed on Server1 expires. You discover that all email messages sent to adatum.com remain in the queue on Server1. On Server1, you install a new certificate from a trusted third-party. You need to ensure that the email messages are delivered to adatum.com. What should you do?
A. Assign the new certificate to the IIS service.
B. Send the new certificate to the administrator at adatum.com.
C. Assign the new certificate to the SMTP service.
D. Create a new send connector that contains an address space to adatum.com.
Correct Answer: C
QUESTION 3
A user fails to connect to his mailbox by using Outlook Anywhere. The user successfully connects to the mailbox by using an Exchange ActiveSync-enabled mobile device and Outlook Web App. You need to identify what prevents the users from connecting to the mailbox by using Outlook Anywhere. Which tool should you use?
A. Microsoft Outlook
B. Microsoft Exchange Server Deployment Assistant
C. Microsoft Exchange RPC Extractor
D. Microsoft Exchange Server Profile Analyzer
E. Microsoft Exchange Server User Monitor
F. Microsoft Exchange Load Generator
G. Exchange Remote Connectivity Analyzer
H. Exchange Server MAPI Editor
Correct Answer: G
2018 New Pass4isture Microsoft 70-410 Dumps Version: This exam is part one of a series of three exams that test the skills and knowledge necessary to implement a core Windows Server 2012 infrastructure in an existing enterprise environment. Passing this exam validates a candidate's ability to implement and configure Windows Server 2012 core services, such as Active Directory and the networking services. Passing this exam along with the other two exams confirms that a candidate has the skills and knowledge necessary for implementing, managing, maintaining, and provisioning services and infrastructure in a Windows Server 2012 environment.
QUESTION 1
Your network contains an Active Directory domain named contoso.com. All client computer accounts are in an organizational unit (OU) named AllComputers. Client computers run either windows 7 or Windows 8.
You create a Group Policy object (GPO) named GP1.
You link GP1 to the AllComputers OU.
You need to ensure that GP1 applies only to computers that have more than 8 GB of memory. What should you configure?
A. The Security settings of GP1
B. The Block Inheritance option for AllComputers
C. The Security settings of AllComputers
D. The WMI filter for GP1
Correct Answer: D
Explanation
Explanation/Reference:
Windows Management Instrumentation (WMI) filters allow you to dynamically determine the scope of Group Policy objects (GPOs) based on attributes of the target computer. When a GPO that is linked to a WMI filter is applied on the target computer, the filter is evaluated on the target computer. If the WMI filter evaluates to false, the GPO is not applied (except if the client computer is running Windows Server, in which case the filter is ignored and the GPO is always applied).If the WMI filter evaluates to true, the GPO is applied.
References: Training Guide: Installing and Configuring Windows Server 2012 R2: Chapter 10: Implementing Group Policy, p.470, 482
QUESTION 2
Your network contains multiple subnets. On one of the subnets, you deploy a server named Server1 that runs Windows Server 2012 R2. You install the DNS Server server role on Server1, and then you create a standard primary zone named contoso.com.
You need to ensure that client computers can resolve single-label names to IP addresses. What should you do first?
A. Create a reverse lookup zone.
B. Convert the contoso.com zone to an Active Directory-integrated zone.
C. Create a GlobalNames zone.
D. Configure dynamic updates for contoso.com.
Correct Answer: C
Explanation
Explanation/Reference:
You should use GlobalNames zone to take advantage of single-label names. This will also ensure that the zone remains valid.
References:
QUESTION 3
Your network contains an Active Directory domain named contoso.com. The DNS zone for contoso.com is Active-Directory integrated. The domain contains 500 client computers. There are an additional 20 computers in a workgroup. You discover that every client computer on the network can add its record to the contoso.com zone. You need to ensure that only the client computers in the Active Directory domain can register records in the contoso.com zone. What should you do?
A. Sign the contoso.com zone by using DNSSEC.
B. Configure the Dynamic updates settings of the contoso.com zone.
C. Configure the Security settings of the contoso.com zone.
D. Move the contoso.com zone to a domain controller that is configured as a DNS server.
Correct Answer: B
Explanation
Note: Pass4itsure provides thousands of latest examinations training materials especially for IT certifications. Pass4itsure not only provide key knowledge points and detailed questions answers and explanations but also excellent after-sale service. You purchase latest practice exam online, you will not only get exam materials but also tracking service.
Recommended Pass4itsure Google PDF:
Free Pass4itsure Microsoft Google Drive: https://drive.google.com/drive/folders/0BwxjZr-ZDwwWYmR6NGh4WDBTNDQ
Free Pass4itsure Cisco Google Drive: https://drive.google.com/drive/folders/0BwxjZr-ZDwwWeVpTdDR1WmJrdVk
Recommended Pass4itsure Youtube Video Training
Pass4itsure Youtube site: https://www.youtube.com/channel/UCLbEVAC-RrG065OIsenPTVw/videos
View pass4itsure video tutorials about the variety of question types on Microsoft exams. You can also be able to make use of the audio exam, video exam and brain dumps for passing and excelling exam in pass4itsure.
Pass4itsure Promo Code 15% Off
Search for: Pass4itsure +"keyword" in Google,Bing,Yahoo,ect. And You will enjoy 15% Pass4itsure promo code always & forever! Use above discount coupon code "[email protected]" to get 15% discount when purchasing any new exam products from pass4itsure.com. The more pass4itsure 15% discount code information at: https://www.work2you.org/pass4itsure-promo-code-15-off/
Who can share new Microsoft 70-742 dumps? The Identity with Windows Server 2016 ( 70-742 Windows Server ) exam is a 97 questions assessment in pass4itsure that is associated with the MCSA certification. Welcome to buy 100% guarantee Microsoft 70-742 dumps Windows Server exam materials Identity with Windows Server 2016 Youtube online free share. "Identity with Windows Server 2016" is the exam name of Pass4itsure Microsoft 70-742 dumps test which designed to help candidates prepare for and pass the Microsoft 70-742 exam. You can use our samples first to experience the effect of our software, and we believe that you can realize our profession and efforts by researching and developing Microsoft https://www.pass4itsure.com/70-742.html dumps materials exam software from samples of Microsoft 70-742 dumps materials.
[Ensure Pass4itsure 70-742 Dumps Exam From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWZDZVWjB6Wno5dzg
[Ensure Pass4itsure 1Y0-371 Dumps Exam From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWekxPNnBJU1N6WWc
Latest and Most Accurate Pass4itsure 70-742 Dumps Exam Q&As(1-16)
QUESTION 1
What is the essential difference between an `Ethical Hacker' and a `Cracker'?
A. The ethical hacker does not use the same techniques or skills as a cracker.
B. The ethical hacker does it strictly for financial motives unlike a cracker.
C. The ethical hacker has authorization from the owner of the target.
D. The ethical hacker is just a cracker who is getting paid.
70-742 exam Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
The ethical hacker uses the same techniques and skills as a cracker and the motive is to find the security breaches before a cracker does. There is nothing that says that a cracker does not get paid for the work he does, a ethical hacker has the owners authorization and will get paid even if he does not succeed to penetrate the target.
QUESTION 2
What does the term "Ethical Hacking" mean?
A. Someone who is hacking for ethical reasons.
B. Someone who is using his/her skills for ethical reasons.
C. Someone who is using his/her skills for defensive purposes.
D. Someone who is using his/her skills for offensive purposes.
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Ethical hacking is only about defending your self or your employer against malicious persons by using the same techniques and skills.
QUESTION 3
Who is an Ethical Hacker?
A. A person who hacks for ethical reasons
B. A person who hacks for an ethical cause
C. A person who hacks for defensive purposes
D. A person who hacks for offensive purposes
70-742 dumps Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
The Ethical hacker is a security professional who applies his hacking skills for defensive purposes.
QUESTION 4
What is "Hacktivism"?
A. Hacking for a cause
B. Hacking ruthlessly
C. An association which groups activists
D. None of the above
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
The term was coined by author/critic Jason Logan King Sack in an article about media artist Shu Lea Cheang. Acts of hacktivism are carried out in the belief that proper use of code will have leveraged effects similar to regular activism or civil disobedience.
QUESTION 5
Where should a security tester be looking for information that could be used by an attacker against an organization? (Select all that apply)
A. CHAT rooms
B. WHOIS database
C. News groups
D. Web sites
E. Search engines
F. Organization's own web site
70-742 pdf Correct Answer: ABCDEF
Explanation
Explanation/Reference:
Explanation:
A Security tester should search for information everywhere that he/she can access. You never know where you find that small piece of information that could penetrate a strong defense.
QUESTION 6
What are the two basic types of attacks?Choose two.
A. DoS
B. Passive
C. Sniffing
D. Active
E. Cracking
Correct Answer: BD
Explanation
Explanation/Reference:
Explanation:
Passive and active attacks are the two basic types of attacks.
QUESTION 7
The United Kingdom (UK) he passed a law that makes hacking into an unauthorized network a felony.
The law states:
Section1 of the Act refers to unauthorized access to computer material. This states that a person commits an offence if he causes a computer to perform any function with intent to secure unauthorized access to any program or data held in any computer. For a successful conviction under this part of the Act, the prosecution must prove that the access secured is unauthorized and that the suspect knew that this was the case. This section is designed to deal with common or-graden hacking. Section 2 of the deals with unauthorized access with intent to commit or facilitate the commission of further offences. An offence is committed under Section 2 if a Section 1 offence has been committed and there is the intention of committing or facilitating a further offense (any offence which attacks a custodial sentence of more than five years, not necessarily one covered but the Act). Even if it is not possible to prove the intent to commit the further offence, the Section 1 offence is still committed. Section 3 Offences cover unauthorized modification of computer material, which generally means the creation and distribution of viruses. For conviction to succeed there must have been the intent to cause the modifications and knowledge that the modification had not been authorized
What is the law called?
A. Computer Misuse Act 1990
B. Computer incident Act 2000
C. Cyber Crime Law Act 2003
D. Cyber Space Crime Act 1995
70-742 vce Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Computer Misuse Act (1990) creates three criminal offences:
QUESTION 8
Which of the following best describes Vulnerability?
A. The loss potential of a threat
B. An action or event that might prejudice security
C. An agent that could take advantage of a weakness
D. A weakness or error that can lead to compromise
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
A vulnerability is a flaw or weakness in system security procedures, design or implementation that could be exercised (accidentally triggered or intentionally exploited) and result in a harm to an IT system or activity.
QUESTION 9
Steven works as a security consultant and frequently performs penetration tests for Fortune 500 companies. Steven runs external and internal tests and then creates reports to show the companies where their weak areas are. Steven always signs a non-disclosure agreement before performing his tests. What would Steven be considered?
A. Whitehat Hacker
B. BlackHat Hacker
C. Grayhat Hacker
D. Bluehat Hacker
70-742 exam Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
A white hat hacker, also rendered as ethical hacker, is, in the realm of information technology, a person who is ethically opposed to the abuse of computer systems. Realization that the Internet now represents human voices from around the world has made the defense of its integrity an important pastime for many. A white hat generally focuses on securing IT systems, whereas a black hat (the opposite) would like to break into them.
QUESTION 10
Which of the following act in the united states specifically criminalizes the transmission of unsolicited commercial e mail(SPAM) without an existing business relationship.
A. 2004 CANSPAM Act
B. 2003 SPAM Preventing Act
C. 2005 US-SPAM 1030 Act
D. 1990 Computer Misuse Act
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
The CAN-SPAM Act of 2003 (Controlling the Assault of Non-Solicited Pornography and Marketing Act) establishes requirements for those who send commercial email, spells out penalties for spammers and companies whose products are advertised in spam if they violate the law, and gives consumers the right to ask emailers to stop spamming them. The law, which became effective January 1, 2004, covers email whose primary purpose is advertising or promoting a commercial product or service, including content on a Web site. A "transactional or relationship message" email that facilitates an agreed-upon transaction or updates a customer in an existing business relationship may not contain false or misleading routing information, but otherwise is exempt from most provisions of the CAN-SPAM Act.
QUESTION 11
ABC.com is legally liable for the content of email that is sent from its systems, regardless of whether the message was sent for private or business-related purpose. This could lead to prosecution for the sender and for the company's directors if, for example, outgoing email was found to contain material that was pornographic, racist or likely to incite someone to commit an act of terrorism. You can always defend yourself by "ignorance of the law" clause.
A. True
B. False
70-742 dumps Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
Ignorantia juris non excusat or Ignorantia legis neminem excusat (Latin for "ignorance of the law does not excuse" or "ignorance of the law excuses no one") is a public policy holding that a person who is unaware of a law may not escape liability for violating that law merely because he or she was unaware of its content; that is, persons have presumed knowledge of the law. Presumed knowledge of the law is the principle in jurisprudence that one is bound by a law even if one does not know of it. It has also been defined as the "prohibition of ignorance of the law".
QUESTION 12
You are footprinting Acme.com to gather competitive intelligence. You visit the acme.com websire for contact information and telephone number numbers but do not find it listed there. You know that they had the entire staff directory listed on their website 12 months ago but now it is not there. How would it be possible for you to retrieve information from the website that is outdated?
A. Visit google search engine and view the cached copy.
B. Visit Archive.org site to retrieve the Internet archive of the acme website.
C. Crawl the entire website and store them into your computer.
D. Visit the company's partners and customers website for this information.
Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
The Internet Archive (IA) is a non-profit organization dedicated to maintaining an archive of Web and multimedia resources. Located at the Presidio in San Francisco, California, this archive includes "snapshots of the World Wide Web" (archived copies of pages, taken at various points in time), software, movies, books, and audio recordings (including recordings of live concerts from bands that allow it). This site is found at www.archive.org.
QUESTION 13
User which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
A. 18 U.S.C 1029 Possession of Access Devices
B. 18 U.S.C 1030 Fraud and related activity in connection with computers
C. 18 U.S.C 1343 Fraud by wire, radio or television
D. 18 U.S.C 1361 Injury to Government Property
E. 18 U.S.C 1362 Government communication systems
F. 18 U.S.C 1831 Economic Espionage Act
G. 18 U.S.C 1832 Trade Secrets Act
70-742 pdf Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
QUESTION 14
Which of the following activities will NOT be considered as passive footprinting?
A. Go through the rubbish to find out any information that might have been discarded.
B. Search on financial site such as Yahoo Financial to identify assets.
C. Scan the range of IP address found in the target DNS database.
D. Perform multiples queries using a search engine.
Correct Answer: C
Explanation
Explanation/Reference:
Explanation:
Passive footprinting is a method in which the attacker never makes contact with the target systems. Scanning the range of IP addresses found in the target DNS is considered making contact to the systems behind the IP addresses that is targeted by the scan.
QUESTION 15
Which one of the following is defined as the process of distributing incorrect Internet Protocol (IP) addresses/names with the intent of diverting traffic?
A. Network aliasing
B. Domain Name Server (DNS) poisoning
C. Reverse Address Resolution Protocol (ARP)
D. Port scanning
70-742 vce Correct Answer: B
Explanation
Explanation/Reference:
Explanation:
This reference is close to the one listed DNS poisoning is the correct answer. This is how DNS DOS attack can occur. If the actual DNS records are unattainable to the attacker for him to alter in this fashion, which they should be, the attacker can insert this data into the cache of there server instead of replacing the actual records, which is referred to as cache poisoning.
QUESTION 16
You are footprinting an organization to gather competitive intelligence. You visit the company's website for contact information and telephone numbers but do not find it listed there. You know that they had the entire staff directory listed on their website 12 months ago but not it is not there. How would it be possible for you to retrieve information from the website that is outdated?
A. Visit google's search engine and view the cached copy.
B. Visit Archive.org web site to retrieve the Internet archive of the company's website.
C. Crawl the entire website and store them into your computer.
D. Visit the company's partners and customers website for this information.
Correct Answer: B
Explanation
Explanation/Reference:
It is very normal to be afraid of the exam, especially such difficult exam like Microsoft 70-742 dumpsexam. We know that encouragement alone cannot really improve your confidence in exam, so we provide the most practical and effective test software to help you pass the Microsoft 70-742 dumps exam. "Identity with Windows Server 2016", also known as 70-742 exam, is a Microsoft certification which covers all the knowledge points of the real Microsoft exam. Pass4itsure Microsoft 70-742 dumps exam questions answers are updated (97 Q&As) are verified by experts. The associated certifications of https://www.pass4itsure.com/70-742.html dumps is MCSA.
Read More Youtube: https://youtu.be/D7ATUdX4E14
What is the best way to prepare for the Microsoft 70-410 dumps exam? The Installing and Configuring Windows Server 2012 ( 70-410 Windows Server ) exam is a 503 Q&As assessment in pass4itsure that is associated with the MCP, MCSA, MCSE certification."Installing and Configuring Windows Server 2012" is the exam name of Pass4itsure Microsoft 70-410 dumps test which designed to help candidates prepare for and pass the Microsoft 70-410 exam. This 70-410 dumps exam is intended for individuals who plan to implement, use, maintain, or support Microsoft Dynamics CRM 2015 Sales and Customer Service applications in their organizations.
Helpful Microsoft https://www.pass4itsure.com/70-410.html dumps Windows Server 2012 exam questions video tests download. This audience typically includes sales operations managers, customer service managers, service schedulers, administrators, office managers, executives, and consultants who want to demonstrate a foundational understanding of the application functionality.
[EnsurePass4itsure 70-410 Dumps Exam From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWemRUYmFFQVdJM1k
[Ensure Pass4itsure 70-412 Dumps Exam From Google Drive]:https://drive.google.com/open?id=0BwxjZr-ZDwwWTVhyb3I4T3F4blE
Latest and Most Accurate Pass4itsure 70-410 Dumps Exam Q&As:
QUESTION 66
You have an existing Active Directory site named Site1. You create a new Active Directory site and name it Site2. You need to configure Active Directory replication between Site1 and Site2. You install a new domain controller. You create the site link between Site1 and Site2. What should you do next?
A. Use the Active Directory Sites and Services console to configure a new site link bridge object.
B. Use the Active Directory Sites and Services console to decrease the site link cost between Site1 and Site2.
C. Use the Active Directory Sites and Services console to assign a new IP subnet to Site2. Move the new domain controller object to Site2.
D. Use the Active Directory Sites and Services console to configure the new domain controller as a preferred bridgehead server for Site1.
70-410 exam Correct Answer: C
QUESTION 67
Your company has an Active Directory forest. Not all domain controllers in the forest are configured as Global Catalog Servers. Your domain structure contains one root domain and one child domain. You modify the folder permissions on a file server that is in the child domain. You discover that some Access Control entries start with S-1-5-21 and that no account name is listed. You need to list the account names. What should you do?
A. Move the RID master role in the child domain to a domain controller that holds the Global Catalog.
B. Modify the schema to enable replication of the friendlynames attribute to the Global Catalog.
C. Move the RID master role in the child domain to a domain controller that does not hold the Global Catalog.
D. Move the infrastructure master role in the child domain to a domain controller that does not hold the Global Catalog.
Correct Answer: D
QUESTION 68
Your company has an Active Directory domain. You log on to the domain controller. The Active Directory Schema snap-in is not available in the Microsoft Management Console (MMC). You need to access the Active Directory Schema snap-in. What should you do?
A. Register Schmmgmt.dll.
B. Log off and log on again by using an account that is a member of the Schema Admins group.
C. Use the Ntdsutil.exe command to connect to the schema master operations master and open the schema for writing.
D. Add the Active Directory Lightweight Directory Services (AD/LDS) role to the domain controller by using Server Manager.
70-410 dumps Correct Answer: A
QUESTION 69
Your network contains a domain controller that is configured as a DNS server. The server hosts an Active Directory-integrated zone for the domain. You need to reduce how long it takes until stale records are deleted from the zone. What should you do?
A. From the configuration directory partition of the forest, modify the tombstone lifetime.
B. From the configuration directory partition of the forest, modify the garbage collection interval.
C. From the aging properties of the zone, modify the no-refresh interval and the refresh interval.
D. From the start of authority (SOA) record of the zone, modify the refresh interval and the expire interval.
Correct Answer: C
QUESTION 70
You have an Active Directory domain named contoso.com. You have a domain controller named Server1 that is configured as a DNS server. Server1 hosts a standard primary zone for contoso.com. The DNS configuration of Server1 is shown in the exhibit. (Click the Exhibit button.) You discover that stale resource records are not automatically removed from the contoso.com zone. You need to ensure that the stale resource records are automatically removed from the contoso.com zone.
What should you do?
A. Set the scavenging period of Server1 to 0 days.
B. Modify the Server Aging/Scavenging properties.
C. Configure the aging properties for the contoso.com zone.
D. Convert the contoso.com zone to an Active Directory-integrated zone.
70-410 pdf Correct Answer: C
QUESTION: 71
Which three BusinessObjects Enterprise XI tasks support XML exporting in Crystal Reports 2008? (Choose three.)
A. Viewing B.
Auditing C.
Publishing
D. Scheduling
Answer: A, C, D
QUESTION: 72
Which statement is true regarding the Object Linking Wizard?
A. Enables report designers to define an URL.
B. Enables report designers to define how a subreport is linked to the main report.
C. Enables report designers to specify how an Xcelsius chart is linked in a report.
D. Enables report designers to specify the order in which subreports should be processed.
70-410 vce Answer: A
QUESTION: 73
Which three procedures will create a second Report Header section named "Report Header b." (Choose three.)
A. Working in the Design window, right-click the grey area containing the section name Report Header and click Insert Line in the shortcut menu to create Report Header b.
B. Working in the Design window, right-click the grey area containing the section name Report Header and click Insert Section Below in the shortcut menu to create Report Header b.
C. On the Common tab of the Section Expert, highlight the Report Header and click the Insert button at the top of the window. Click OK to create Report Header b.
D. Working in the Design window, point to the left boundary of the Report Header until the section splitting cursor appears and drag it down to split the section into Report Header a and Report Header b.
Answer: B, C, D
QUESTION: 74
You create the following array in a new Crystal report: ["dog", "cat", 1.25, True] Why do you get an error when you save the formula?
A. The Boolean value must be the first array element.
B. The array elements are not in alphabetical order.
C. You cannot summarize the elements in an array.
D. You cannot have more than one data type in an array.
70-410 exam Answer: D

If you choose the help of Pass4itsure, we will spare no effort to help you pass the exam. Moreover, we also provide you with a year of free after-sales service to update the 70-410 dumps exam practice questions and answers. Do not hesitate! Please select Pass4itsure, it will be the best guarantee for you to pass https://www.pass4itsure.com/70-410.html dumps exam cram. Now please add Pass4itsure to your shopping cart.
Microsoft 70-410 Dumps Youtube: https://youtu.be/y5xJFyZjV5c
Posted by: aideaidesylvestere0267087.blogspot.com
Source: https://www.exammodule.com/category/microsoft/
Post a Comment